- 1. Introduction
- 2. Configuring a JOnAS instance
- 2.1. Configuring JOnAS Environment : JONAS_BASE
- 2.2. Configuring the communication protocol and JNDI
- 2.3. Configuring the logging System
- 2.4. Configuring JOnAS Services
- 2.4.1. cmi service configuration
- 2.4.2. db service configuration
- 2.4.3. depmonitor service configuration
- 2.4.4. dbm service configuration
- 2.4.5. discovery service configuration
- 2.4.6. ear service configuration
- 2.4.7. EJB2 Service configuration
- 2.4.8. Ejb3 service configuration
- 2.4.9. ha service configuration
- 2.4.10. jmx service configuration
- 2.4.11. jtm service configuration
- 2.4.12. mail service configuration
- 2.4.13. registry service configuration
- 2.4.14. resource service configuration
- 2.4.15. security service configuration
- 2.4.16. versioning service configuration
- 2.4.17. wc service configuration
- 2.4.18. web service configuration
- 2.4.19. wm service configuration
- 2.4.20. ws service configuration
- 2.5. Configuring Security
- 2.6. Configuring JDBC Resource Adapters
- 2.7. Configuring JMS Resource Adapters
- 2.8. Configuring JDBC DataSources
- 3. Cluster configuration
- 4. Domain management
- 5. EasyBeans Server Configuration File
- 6. Glossary
Configuration is a task that may be more or less complex. Configuring a unique instance is obviously easier than configuring a cluster of servers.
Configuration task consists mainly in customizing a set of JOnAS configuration files that compose the JOnAS environment see Section 2.1, “Configuring JOnAS Environment : JONAS_BASE”.
First of all, some terms used is this document must be defined:
A server, or JOnAS instance, is a java process started via one of the jonas bootstrap or jonas start commands, or via the administration tool Java EE.
Several servers may run on the same physical host.
When a server starts, services are started.
A service typically provides system resources to containers. Most of the components of the JOnAS application server are pre-defined services. However, it is possible and easy for an advanced user to define a new service and to integrate it into JOnAS.
A container consists of a set of Java classes that implement the Java EE specification. The role of the container is to provide the facilities for executing Java EE components.
There are three types of containers:
-
EJB container in which Enterprise JavaBeans are deployed and run
-
Web container for JSPs and servlets
-
Client container
A domain represents an administration perimeter which is under the control of an administration authority.
This perimeter contains management targets like servers and clusters.
If a domain contains several elements, it provides at least one common administration point represented by a master server.
A master is a JOnAS instance having particular management capabilities within the domain:
-
it is aware of the domain's topology
-
it allows management and monitoring of all the elements belonging to the domain
A cluster is a group of JOnAS servers having common properties within a domain. It usually allows to run a J2EE application, or a J2EE module, on the cluster members as if they were a single server. The objective is to achieve applications scalability and high availability.
JOnAS supports several cluster types:
-
Clusters for Web level load-balancing
-
Clusters for high availability of Web components
-
Clusters for EJB level load-balancing
-
Clusters for high availability of EJB components
-
Clusters for JMS destination scalability and high availability
-
Clusters for administration purpose which facilitate management operations like deployment /undeployment.
From the administrator point of view, a cluster represents a single administration target.
Note that a particular JOnAS server may belong to zero, one or more clusters.
- 2.1. Configuring JOnAS Environment : JONAS_BASE
- 2.2. Configuring the communication protocol and JNDI
- 2.3. Configuring the logging System
- 2.4. Configuring JOnAS Services
- 2.4.1. cmi service configuration
- 2.4.2. db service configuration
- 2.4.3. depmonitor service configuration
- 2.4.4. dbm service configuration
- 2.4.5. discovery service configuration
- 2.4.6. ear service configuration
- 2.4.7. EJB2 Service configuration
- 2.4.8. Ejb3 service configuration
- 2.4.9. ha service configuration
- 2.4.10. jmx service configuration
- 2.4.11. jtm service configuration
- 2.4.12. mail service configuration
- 2.4.13. registry service configuration
- 2.4.14. resource service configuration
- 2.4.15. security service configuration
- 2.4.16. versioning service configuration
- 2.4.17. wc service configuration
- 2.4.18. web service configuration
- 2.4.19. wm service configuration
- 2.4.20. ws service configuration
- 2.5. Configuring Security
- 2.6. Configuring JDBC Resource Adapters
- 2.7. Configuring JMS Resource Adapters
- 2.8. Configuring JDBC DataSources
JOnAS is pre-configured and ready to be used directly. The Getting Started book has shown that a very sample example may be run after JOnAS installation without any configuration task. But as soon as your application needs to use resources specific to the execution environment, configuration is mandatory.
In this chapter we will see in a first part where are the configuration files and then what that can be configured
JOnAS distribution contains a number of configuration files in
$JONAS_ROOT/conf directory. These
files can be edited to change the default configuration. However, it is
recommended that the configuration files needed by a specific
application running on JOnAS be
placed in a separate location. This is done by using an additional
environment variable called JONAS_BASE.
JOnAS configuration files are read from the $JONAS_BASE/conf directory. If JONAS_BASE is not defined, it is automatically initialized to $JONAS_ROOT.
JONAS_BASE has the following structure:
-
the
conf/directory -
the
deploydirectoryis the main location used for deployment.
At JOnAS startup time all the Java EE archives and OSGi bundles are deployed in the following order:
-
bundles OSGi,
-
rar archives,
-
ejb archives,
-
war archives,
-
ear archives,[1]
Then this directory is periodically polled in order to deploy new archives. For more information have a look at the depmonitor service configuration
-
-
the
libdirectory [2]Used for extending class loaders. It contains four sub directories:
directory description appsfor apps ClassLoader commonsfor the commons ClassLoader extthe same usage than commonstoolsfor the tools ClassLoader -
the
logsdirectorywhere the log files are created at run-time
-
the
workdirectory
-
Create a JONAS_BASE template from scratch :
export JONAS_BASE=~/my_jonas_base cd $JONAS_ROOT ant -f build-jb.xml create_jonas_base
This will copy all the required files and create all the directories needed.
-
Another way to create a JONAS_BASE template from scratch :
export JONAS_BASE=~/my_jonas_base newjb
The JONAS_BASE created with the command newjb is well suited to run the JOnAS conformance test suite without any additional configuration.
In order to customize a JONAS_BASE with specific values for some properties (like port number, services, protocol etc...), you must edit the
$JONAS_ROOT/build-jb.propertiesfile or$HOME/jb.config/conf/jonas-newjb.propertiesfile before running newjb. You may also modify the generated files in$JONAS_BASE/conf. For more information see the description of the newjb command in Commands Reference Guide.
This directory contains configuration files in various format (properties file, xml files).
The main configuration file is jonas.properties but there are also:
-
Templates for configuring access to databases (Oracle, PostgreSQL, Sybase, DB2, MySQL, HSQLDB, InterBase, FirebirdSQL, Mckoi SQL, InstantDB ) respectively in Oracle1.properties, PostgreSQL1.properties,etc... All these databases have been tested with JOnAS.
-
Mail resources templates : MailMimePartDS1.properties, MailSession1.properties
-
JORAM configuration files : a3debug.cfg, a3servers.xml, joramAdmin.xml
-
carol.properties, jacorb.properties, jonathan.xml [3] for configuring the RMI implementation used through CAROL.
-
Configuration files for clustering : clusterd.xml, domain.xml, jgroups-ha.xml, jgroups-cmi.xml,jk2.properties
-
Configuration files related to security: jaas.config, java.policy, jonas-realm.xml
-
Web container configuration files:
-
server.xml, context.xml ,web.xml for Tomcat,
-
jetty5.xml jetty5-webdefault.xml for Jetty.
-
-
Web services configuration files: jaxr.properties, uddi.properties, file1.properties.
-
Client container configuration file: jonas-client.properties
-
JOnAS traces configurations files: trace.properties, traceclient.properties
-
Speedo configuration file: speedo-jdo.properties
-
Transaction recovery configuration file : jotm.properties
-
P6Spy options file: spy.properties
-
Thread management framework configuration file: jonas_areas.xml
-
Fractal deployment framework configuration file: execute.properties
-
Java Service Wrapper configuration file: wrapper.conf
Most of these files are described in following sections.
$JONAS_BASE/conf/jonas.properties is the key file for configuring JOnAS.
This file is used for:
# Enable the Security context propagation for jrmp jonas.security.propagation true # Enable the rmi Security manager jonas.security.manager true # Enable csiv2 security propagation for rmi/iiop jonas.csiv2.propagation true # Enable the Transaction context propagation jonas.transaction.propagation true # Set the name of log configuration file to trace.properties jonas.log.configfile trace
Properties are self commented.
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
setting jonas.security.manager to
carol.jvm.rmi.local.registry=true |
Here is the list of default services activated at starting time:
jonas.services registry,jmx,jtm,db,security,mail,wm,resource,ejb2,ejb3,ws,web,ear,depmonitor
The possible services are:
registry,jmx,security,jtm,db,mail,wm,wc,dbm,resource,cmi,ha,ejb2,ejb3,ws,versioning,web,ear,depmonitor,discovery
- db
-
this service is used for launching a Java database implementation. By default, HSQLDB java database is used.
- dbm
-
the database service is needed by application components that require access to one or several relational databases. It may be an alternative to the usage of a JDBC resource adapter via the resource service.
- depmonitor
-
the depmonitor service is used to control deployment process in JOnAS.
- cmi
-
the CMI service provides support for the clustering of RMI objects.
- discovery
-
this service allows dynamic administration of management domains
- ear
- ejb2
-
the EJB container service provides support for EJB components.
- ejb3
-
the EJB3 container service provides supports for EJB3 components
- ha
-
the High Availability service provides stateful session beans replication.
- jmx
-
this service is needed in order to administrate the JOnAS servers and the JOnAS services via a JMX-based administration console.
- jtm
-
the transaction manager service is used for support of distributed transactions with JOTM.
-
this service is required by applications that need to send e-mail messages.
- registry:
-
this service is used for binding remote objects and resources that will later be accessed via JNDI. It is automatically launched before all the other services when starting JOnAS.
- resource
-
this service is needed to use resource adapters conformant to the Java EE Connector Architecture Specification
- security
-
this service is needed for enforcing security at runtime.
- versioning
-
this service has been designed for dynamic redeployment of applications,without any application downtime and without users' sessions being lost:.
- wc
-
the WorkCleaner service cleans up periodically the work directory of the JOnAS server.
- web
-
the WEB container service provides support for web components (as Servlets and JSP). JOnAS provides two implementations of this service, one based on Tomcat and another on Jetty.
- wm
-
the WorkManager service provides a manageable Thread Pool for resource adapters components.
- ws
-
the WebServices service provides support for WebServices (WSDL publication).
Services will be started in the order in which they appear in the list. Therefore, the following constraints should be considered:
-
jtm must precede the following services: dbm, resource, ejb.
-
ejb, ws, web must precede ear.
-
if security service uses realm in database it must be after dbm or resource.
-
the services used by the application components must be listed before the container service used to deploy these components. For example, if the application contains EJBs that need send e-mail messages, mail must precede ejb in the list of required services.
registry can be omitted from the list because this service is automatically launched if it is not already activated by another previously started server. This is also true for jmx, since it is automatically launched after the registry.
Configuration parameters for services follow a strict naming convention: a service XX will be configured via a set of properties:
jonas.service.XX.foo something
jonas.service.XX.bar else
each service XX must contain the property jonas.service.XX.class indicating the name of the java class that implements the service:
jonas.service.XX.class aa.bb.XXImpl
This allow experimented user to replace built-in service by an alternative implementation.
For example here is the part of
jonas.properties file related to the customization
of jtm service:
###################### JOnAS JTM Transaction service configuration
# Set the name of the implementation class of the jtm service
jonas.service.jtm.class org.ow2.jonas.tm.jotm.JOTMTransactionService
# Set the Transaction Manager launching mode.
# If set to 'true', TM is remote: TM must be already launched in an other JVM.
# If set to 'false', TM is local: TM is going to run into the same JVM
# than the jonas Server.
jonas.service.jtm.remote false
# Set the default transaction timeout, in seconds.
jonas.service.jtm.timeout 60
see Section 2.4, “Configuring JOnAS Services” for a complete description of the services configuration.
JOnAS provides a multi-protocol support through the integration of the CAROL component.
Supported communication protocols are the following:
-
RMI/JRMP is the JRE implementation of RMI on the JRMP protocol. This is the default communication protocol.
-
RMI/IIOP is the JacORB implementation of RMI over the IIOP protocol.
-
IRMI is an RMI implementation that can be used with Open Source JDK that doesn't provide
com.sun.*classes.
For each of these protocols, the clustering of RMI objects can be enabled with the component CMI.
The choice of the protocol is made in the
carol.protocols property of
carol.properties file in JONAS_BASE/conf directory.
carol.protocols=jrmp
carol.protocols=jrmpcarol.jrmp.url=rmi://localhost:1099
carol.jvm.rmi.local.call=false
carol.jvm.rmi.local.registry=false
carol.jrmp.server.port=0
carol.jrmp.interfaces.bind.single=false
|
choice of the protocol or list of protocols |
|
|
connexion url to the RMI registry the hostname (localhost) and port number must be changed if needed. In a distributed configuration changing the hostname is mandatory. |
|
|
if true local calls are optimized: calls to methods of the remote interface are treated as call to local methods (it is not always possible depending on the packaging of the application). |
|
|
if true a local Naming context is used. This must be used only with a collocated registry and it is mandatory when the jonas.security.manager property of jonas.properties is set to true. |
|
|
exported objects will listen on this port for remote method invocations. 0 means random port. Specify a port may be useful when the server run behind a firewall. |
|
|
if true use only a single interface (choosen from the url) when creating the registry. False means use all interfaces available. |
The JacORB implementation of RMI over the IIOP is used. The
configuration file of JacORB is the $JONAS_BASE/conf/jacorb.properties
file.
As for the other protocols RMI over IIOP is ready to used in the
default distribution. It is only for tuning purpose that the $JONAS_BASE/conf/jacorb.properties file
must be customized.
By default the CORBA Naming service is run using the port 2001 (as
it is set in the carol.properties file)
So the only thing to do for working in RMI over IIOP is to set the property protocols in carol.properties:
carol.protocols=iiop # RMI IIOP URL carol.iiop.url=iiop://localhost:2001 carol.iiop.server.port=0carol.iiop.server.sslport=2003
carol.iiop.PortableRemoteObjectClass=org.objectweb.jonas_lib.naming.JacORBPRODelegate
carol.protocols=irmi carol.irmi.url=rmi://localhost:1098carol.irmi.server.port=0
carol.irmi.interfaces.bind.single=false
|
for irmi the default port is 1098 |
||||
|
exported objects will listen on this port for remote method invocations:0 means random port.
|
||||
|
if true use only a single interface when creating the registry (specified in carol.irmi.url property). Default configuration = false(use all interfaces available) |
CMI is the component to use for clustering purpose. It is embedded in the component CAROL.
CMI is just composed of wrappers and interceptors and is fully independant of the implementation of protocol. CMI relies on JGroups group-communication protocol for ensuring the replication of the cluster view. CMI provides jndi high availability, the load-balancing and fail-over at the EJB level.
For using CMI with a protocol (in addition to the activation of
service cmi), a property must be added in
carol.properties:
carol.jrmp.cmi=truecarol.iiop.cmi=true carol.irmi.cmi=false
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
By default, the property is set at true. |
JOnAS can be configured to use several protocols simultaneously.
To do this, just specify a comma-separated list of protocols in the
carol.protocols property of the carol.properties
file. For example:
carol.protocols=iiop,jrmp carol.jrmp.url=rmi://localhost:1099 carol.iiop.url=iiop://localhost:2001
![[Caution]](../../resources/images/caution.png) |
Caution |
|---|---|
|
When iiop is used in a multiprotocol configuration, it must appear at the first position in the protocol list. |
Monolog is the Objectweb solution for logging. It is not only a new logging implementation but can be seen as a bridge between different logging implementations. A library that uses the Monolog API can be used with any logging implementation at runtime.
Furthermore some components of JOnAS like CAROL, JOTM, Tomcat etc... doesn't use the Monolog API but Jakarta commons loggins or log4j or other implementation. However all these components will be configured via the JOnAS Monolog configuration file.
JOnAS Monolog configuration files are:
-
$JONAS_BASE/conf/trace.properties[4]which is the server side Monolog configuration file
-
$JONAS_BASE/conf/traceclient.propertieswhich is used for a client in a client container.
Configuring trace messages inside JOnAS can be done in two ways:
-
Changing the
trace.propertiesfile to configure the traces statically, before the JOnAS Server is run -
Using the jonas admin command or the JonasAdmin administration tool to configure the traces dynamically while the JOnAS Server is running. In this case the modification are not persistent (
trace.propertiesfile is not modified).
Applications make logging calls on logger objects.Loggers are organized in a hierarchical namespace and child loggers may inherit some logging properties from their parents in the namespace. Loggers allocates messages and passes them to handler for output; they uses logging levels in order to decide if they are interested in by a particular message.
In trace.properties it is possible to
define handlers, loggers,
levels:
-
handlers
A handler represents an output, is identified by its name, has a type, and has some additional properties. By default three handlers are used:
-
tty is basic standard output on a console
-
logf is a handler for printing messages on a file
-
mesonly handler used by generation tools for traces without header
Each handler can define the header it will use, the type of logging (console, file, rolling file), and the file name.
The handler properties are the following:
-
type: is the type of the handler that may be:
-
Console : Log stream ends inside
System.outorSystem.err -
File : Log stream is directed into a file
-
Rollingfile : A file set is used to roll the logs
-
JMX : Logging actions are send to the JMX notification system
-
-
pattern:is the message format. A pattern can be composed of elements. An element is prefixed by the % character.The possible items:
-
%h: the thread name
-
%O{1} : the Class name (basename only)
-
%M the method name
-
%L the line number
-
%d the date
-
%l the level
-
%m the message itself
-
%n a new line
-
-
output: is the output filename.
If automatic[5] is used, JOnAS will replace this tag with a file pointing to
$JONAS_BASE/logs/<jonas_name_server>-<timestamp>.logSwitch is used for logging either on
System.outorSystem.errdepending on the level of the log -
fileNumber: is the number of file to use (for RollingFile)
-
maxSize:is the maximal size of the file (for Rolling file)
-
-
loggers
Loggers are identified by names that are structured as a tree. The root of the tree is named root. Each logger is associated with a topic. Topic names are usually based on the package name. Each logger can define the handler it will use and the trace level (see below). By default loggers inherit their level from their parents.
By default handlers assigned to the parent logger are automatically assign to child loggers. Setting 'additivity' to false inform the system that the logger will use only its own set of handlers.[6]
-
levels
the trace levels are the following:
-
ERROR errors. Should always be printed.
-
WARN warning. Should be printed.
-
INFO informative messages.
-
DEBUG debug messages. Should be printed only for debugging.
-
log.config.classname org.objectweb.util.monolog.wrapper.javaLog.LoggerFactoryhandler.tty.type Console
handler.tty.output Switch
handler.tty.pattern %d : %O{1}.%M : %m%n
handler.logf.type File
handler.logf.output automatic
handler.logf.pattern %d : %l : %h : %O{1}.%M : %m%n logger.root.handler.0 tty
logger.root.handler.1 logf
logger.root.level INFO
logger.org.objectweb.level INFO #logger.org.objectweb.jonas_ejb.level DEBUG
handler.mesonly.type Console
handler.mesonly.output Switch handler.mesonly.pattern %m%n logger.org.objectweb.jonas.genic.handler.0 mesonly
logger.org.objectweb.jonas.genic.additivity false
[...]
|
Definition of the wrapper to use: here the java logging API wrapper. |
|
|
Definition of the console handler tty |
|
|
Switch means that the logs will be on System.out or System.err depending of the level of the log. |
|
|
Definition of the message format. here it contains the date followed by ':' the basename of the class followed by '.' the method name followed by ':' the message itself terminated by newline. |
|
|
Definition of the file handler logf |
|
|
Logs are in a file whose name is
|
|
|
Definition of the root logger. It uses handler tty |
|
|
Definition of the root logger: It uses also handler logf |
|
|
Definition of the root logger: level INFO is used for all child loggers if there is no overriden definition |
|
|
This line must be uncommented for setting DEBUG level for the logger used in the jonas_ejb module |
|
|
Definition of the console handler mesonly used by GenIC tool which want to log messages without headers |
|
|
Definition of the handler used by the logger org.objectweb.jonas.genic |
|
|
This logger wants to use its own handler. |
When a problem occurs it may be worth to set some debugging traces in the JOnAS server. It is not easy to know which logger to set to obtain the pertinent traces that may help the debbugging process.
The trace.properties file contains several
commented lines prepared to set loggers in DEBUG level.
Usually the name of loggers are related to the java package name in which it is used.
-
To set debug traces of the EJB container uncomment one or more lines related to logger org.objectweb.jonas_ejb for example:
logger.org.objectweb.jonas_ejb.interp.level DEBUG logger.org.objectweb.jonas_ejb.synchro.level DEBUG logger.org.objectweb.jonas_ejb.tx.level DEBUG
-
To set traces related to resource adapters:
logger.org.objectweb.jonas.jca.level DEBUG logger.org.objectweb.jonas.jca.pool.level DEBUG
-
To set traces into the CAROL library::
logger.org.objectweb.carol.level DEBUG
-
To set traces in JORAM:
logger.fr.dyade.aaa.level DEBUG (for the MOM) # for the JORAM resource adapter: logger.org.objectweb.joram.client.jms.Client.level DEBUG logger.org.objectweb.joram.client.connector.Adapter.level DEBUG
-
To set traces in Tomcat:
-
for all web application :
logger.org.apache.catalina.core.ContainerBase.[jonas].[localhost].level DEBUG
jonas is the attribute name of the element Engine in $JONAS_BASE/conf/server.xml
localhost is the attribute name of the element Host in $JONAS_BASE/conf/server.xml
-
for a particular web application :
logger.org.apache.catalina.core.containerBase.[jonas].[localhost].[jonasAdmin].level DEBUG
jonas is the attribute name of the element Engine in $JONAS_BASE/conf/server.xml
localhost is the attribute name of the element host in $JONAS_BASE/conf/server.xml
jonasAdmin is the name of the web application
![[Note]](../../resources/images/note.png)
Note the attributes debug in elements of $JONAS_BASE/conf/server.xml are not used anymore in Tomcat.
-
-
There are a lot of traces possible for management,discovery,jtm,clustering,mail, ear,...
If Monolog is configured to use the JDK logger it will replace the JDK logger implementation with its own implementation and so all JDK logs are intercepted by Monolog. By default Monolog is configured to use the JDK logger.
There is no special configuration file for Jakarta commons login.If it is used on top of the java logging API it is the same case than the previous section.
JOnAS don't provide the corresponding
jar file so, log4j must be
packaged (.jar file and
log4j.properties) in any application that want
to use it. The log4j.properties file must be
configured correctly.
If log4j is used by several applications it is possible to
centralize the log4j configuration by putting log4j.properties in
$JONAS_BASE/conf and log4j
jar file in $JONAS_BASE/lib/commons.
Here is the list of possible services
registry,jmx,security,jtm,db,mail,wm,wc,dbm,resource,cmi,ha,ejb2,ejb3,ws,versioning,web,ear,depmonitor,discovery
In this chapter we will describe how to configure each service in
the jonas.properties file.
The configuration of the cmi service
is available through the file
$JONAS_BASE/conf/cmi.properties.
Here is the additional configuration in the wake of configurating JNDI protocols.
# CMI InitialContextFactory is preferred when CMI is enabled cmi.context.factory=org.ow2.cmi.jndi.context.CMIInitialContextFactory# Setter class for CMI cmi.setter.class=org.ow2.cmi.config.CentralizedConfig
# Must take a Properties object in parameter cmi.setter.methodProperties=setProperties # Must take a Domain name and a server name in parameter cmi.setter.methodMBean=setMBean # Time to refresh the client view. cmi.client.refresh.time=50000
# Class name of the implementation of the ServerClusterViewManager. cmi.server.impl.class=org.ow2.cmi.controller.server.impl.jgroups.JGroupsClusterViewManager
# Filename of the jgroups conf file cmi.server.impl.jgroups.conf=jgroups-cmi.xml
# Groupname for JGroups cmi.server.impl.jgroups.groupname=G1
# Timeout to wait a reconnection cmi.server.impl.jgroups.reconnection.timeout=30000
# Enable or disable bind of a provider cmi.server.provider.bind=true
# Enable or disable bind of a registry cmi.server.registry.bind=true
# Load factor for the server configured with this file cmi.server.load=100
# Enable or disable registering of clustered objects cmi.server.start.replication=true
# List of provider URLs in order to allow servers having replication disabled to retrieve the cluster view cmi.server.provider.urls=

|
CMI initial context factory - must not be modified |
|
|
Parameters used for the embedded mode (eg. within carol) - must not be modified in the JOnAS context |
|
|
Refresh period of the client view (in ms). For example, it expresses the maximum delay for taking into account a load-balancing policy update. |
|
|
Specifies the protocol implementation that must be used for
replicating the registries. It must implement the
|
|
|
JGroups related parameter (valid if JGroups is set for
implementing the replication protocol, see
|
|
|
JGroups related parameter (valid if JGroups is set for
implementing the replication protocol, see
|
|
|
JGroups related parameter (valid if JGroups is set for
implementing the replication protocol, see
|
|
|
True indicates that the current node will act as a control provider node for CMI, it will serve the cluster view for clients |
|
|
True enables to access to the not clustered objects (EJB) from any clients within the cluster and thus make transparent to the client the distributed registries. |
|
|
Specifies the initial load-factor of the current node used in the weigthed round robin policy. |
|
|
True specifies that a CMI registry must be started (used for hosting the clustered objects), acts as a CMI server. |
|
|
If the CMI registry is not started, this parameter specifies the list of control nodes (urls), acts as a CMI client. In this case, the parameters 3-10 are not used. |
The db service is an optional service that can be used to start a java database server in the same JVM as JOnAS.
By default the database used is HSQLDB.
Here is the part of jonas.properties related to
db service:
###################### JOnAS DB service configuration # # Sets the name of the implementation class of the db service (hsql for example) jonas.service.db.class org.ow2.jonas.db.hsqldb.HsqlDBServiceImpl jonas.service.db.port 9001 jonas.service.db.dbname db_jonas jonas.service.db.users jonas:jonas # Multiple users #jonas.service.db.users jonas:jonas,login:password
Here it is possible to customize :
-
the listening port
-
the database name
-
By default, the user is named jonas with the password jonas. In order to add new users, the property jonas.service.db.users needs to be updated by using a comma separated list as follow:
jonas.service.db.users login:password,anotherlogin:password
The database may be used by Java EE component via
JDBC resource adapters or via the dbm
service. For the former case the same information (listening
port, database name, login,password) must appear in the JOnAS connector deployment descriptor, in the latter they
appear in the $JONAS_BASE/conf/HSQLDB1.properties. So, if
these previous properties must be changed in jonas.properties, they must be
also changed in these files.
The db service has been provided in
the jonas distribution mainly to run easily the JOnAS exemple, without having to set a database
first. For most usages, the JOnAS
users should remove it from the list of services and remove also HSQL1 from
jonas.service.dbm.datasources property in
$JONAS_BASE/conf/jonas.properties file.
For users that choose HSQLDB as database it is highly recommended to
refer to the Hsqldb
User Guide. It is worth to note that the default configuration file
used by HSQLDB server can be found in $JONAS_BASE/work/hsqldb/jonas/db_jonas.properties
directory.
In order to launch several HSQLDB instances, the configuration needs to be duplicated and the new configuration will be prefixed by jonas.service.<mynewdbservice>.
The depmonitor service is required to
deploy J2EE applications in a JOnAS server. Put the application files into the
$JONAS_BASE/deploy directory in order to deploy them.
It is possible to parse anothers directories by setting the directories
property in the service configuration.
The development attribute in the configuration allows to choose if the depmonitor service is in development mode or not :
-
The deployment monitor can be configured to detect at runtime if an application is added, removed or changed to respectively deploy it, undeploy it or redeploy it. This functionnality can be useful during the development phase.
-
For a prodution usage of the JOnAS server, this functionnality can be disabled so that the application files will be deployed only at startup. In this configuration, the jonas admin command or the jonasAdmin user interface will be used to perform deployment actions.
As the parsed directories may contain files that must not be deployed, a list of file exclusions can be defined.
###################### JOnAS Deployment Monitor # # Set the name of the implementation class of the depmonitor service # jonas.service.depmonitor.class org.ow2.jonas.deployablemonitor.DeployableMonitorService jonas.service.depmonitor.development truejonas.service.depmonitor.directories
# List (comma separated) of exclusion patterns (based on names, not directories) jonas.service.depmonitor.exclusions README
The dbm service (database manager
service) allow access to one or more relational databases. It will create
and use DataSource objects. Such a DataSource object
must be configured according to the database that will be used for the
persistence of a bean.
![[Caution]](../../resources/images/caution.png) |
Caution |
|---|---|
|
the recommended way to access to databases is to use the resource service deploying JDBC resource adapter |
The dbm service provides a generic
driver-wrapper that emulates the XADataSource
interface on a regular JDBC driver.It is important to note that this
driver-wrapper does not ensure a real two-phase commit for distributed
database transactions. When it is necessary to use a JDBC2-XA-compliant
driver access to the databases must be done via a JDBC resource adapter XA
compliant (more information can be found in Section 2.6, “Configuring JDBC Resource Adapters”
Here is the part of jonas.properties related to
dbm service:
###################### JOnAS DBM Database service configuration # # Set the name of the implementation class of the dbm service jonas.service.dbm.class org.objectweb.jonas.dbm.DataBaseServiceImpl # Set the jonas DataSources. This enables the JOnAS server to load # the data dources, to load related jdbc drivers, and to register the data # sources into JNDI. # This property is set with a coma-separated list of Datasource properties # file names (without the '.properties' suffix). # Ex: Oracle1,InstantDB1 (while the Datasources properties file names are # Oracle1.properties and InstantDB1.properties) jonas.service.dbm.datasources HSQL1
For the dbm service it is possible to:
-
set a list of datasource names via property jonas.service.dbm.datasources.
for each name XX appearing in this list a
XX.propertiesfile must exist in$JONAS_BASE/conf
Access to a particular database via dbm service is configured in datasource.properties
files that must be located in $JONAS_BASE/conf.
In the JOnAS distribution several templates of datasource.properties files are provided one for Oracle, PostgreSQL, Sybase, DB2, MySQL, HSQLDB, InterBase, FirebirdSQL, Mckoi SQL, InstantDB ) respectively in Oracle1.properties, PostgreSQL1.properties etc...
A complete description of the datasource.properies file can be found inSection 2.8, “Configuring JDBC DataSources”
The role of the discovery service is to enable dynamic domain management. Recall that domain management means management of all the servers running in the domain, from the common administration point represented by a master server.
The discovery service allows a master to detect servers starting and stopping in the domain. Moreover, a master can discover servers there were already running in the domain when it started.
The discovery service implements a greeting mechanism to enforce servers' name unicity in the domain. This mechanism prevents starting a new server in the domain, if a server having the same name is already running in the domain.
There are two available implementations for the discovery service: one based on IP multicast, the other based on JGroups. The former, introduced in JOnAS 4, is deprecated. The latter, has the advantage to allow for cluster daemons detection.
All servers and in the domain must choose the same implementation. The choice is made upon the implementation class name:
###################### JOnAS Discovery service # # Set the name of the implementation class and initialization parameters # JGropus implementation jonas.service.discovery.class=org.ow2.jonas.discovery.jgroups.JgroupsDiscoveryServiceImpl # Uncomment this to set Multicast implementation #jonas.service.discovery.class=org.ow2.jonas.discovery.internal.MulticastDiscoveryServiceImpl
You have to provide initialization parameters in jonas.properties file for:
-
Multicast address and port. These must be identical for all servers in the domain. Use properties:
-
jonas.service.discovery.multicast.address
-
jonas.service.discovery.multicast.port
beware that multicast adresses must be consequently allocated through the network.
-
-
The time-to-live for packets: use property:
-
jonas.service.discovery.ttl
this parameter indicates the number of gateway hops for packets.
-
if ttl = 0 the discovery scope is the host (multicast packet aren't routed to network interfaces).
-
if ttl =1 the discovery scope is limited to the subnetworks the host is attached to (multicast packets cross the network interfaces but will be discarded by the next gateway).
-
if ttl =N>1 the discovery packets may cross N-1 gateways (provided that these gateways are configured to propagate multicast packets).
-
-
In the case of a master server, the jonas.service.discovery.source.port property must be set with an available port number.
-
The greeting mechanism. Use properties:
-
jonas.service.discovery.greeting.port
-
jonas.service.discovery.greeting.timeout
Note that two servers on the same host must have different values in greeting.port property.
-
Example:
jonas.service.discovery.multicast.address=224.224.224.224 jonas.service.discovery.multicast.port=9080 jonas.service.discovery.ttl=1 # For a master server, configure the client source port with this property jonas.service.discovery.source.port=9888 # A multicast greeting message is sent out when discovery service is started. # The starting server listens at the port jonas.service.discovery.greeting.port # (default 9899) for a response for jonas.service.discovery.greeting.timeout miliseconds # (default 1000 ms). If a pre-existing server has the same server name as this one, # this server's discovery service will be terminated. jonas.service.discovery.greeting.port=9899 jonas.service.discovery.greeting.timeout=1000
JGropups configuration being more complex, a specific configuration file have to be used. The name of this file is given by the jonas.service.discovery.jgroups.conf property. Two other properties have to be initialized:
-
The name of the JGroups group used by the the discovery service to exchange messages.
-
jonas.service.discovery.group.name
-
-
The reconnection timeout for the JGroups channel.
-
jonas.service.discovery.group.reconnection.timeout
-
Example:
jonas.service.discovery.jgroups.conf=jgroups-discovery.xml jonas.service.discovery.group.name=JGroupsDiscovery jonas.service.discovery.group.reconnection.timeout=5000
You can find in JOnAS distribution, under
JONAS_ROOT/conf, a jgroups-discovery.xml
file. This file containes a JGroups stack configuration for the UDP
protocol.
In order to be detected by a master server, a cluster daemon has to
be properly configured. This is achieved by using a
discovery entry in the clusterd.xml
configuration file. The configuration properies are:
-
The JGroups group name
-
The JGroups stack configuration file name
-
A
booleanallowing to activate (iftrue) the discovery.
Example:
<discovery>
<group-name>JGroupsDiscovery</group-name>
<stack-file>jgroups-discovery.xml</stack-file>
<start-up>true</start-up>
</discovery>
The ear service allows deployment of
complete Java EE
applications (including ejb-jar,
war and rar files packed in an
ear file). This service is based on
the web service for deploying the included
wars, the ejb2 or ejb3 service
for deploying the EJB containers for the included ejb-jars and the resource service for deploying the included rars.
In development mode, as all other Java EE archives ear archives can be
deployed automatically as soon as they are copied under
$JONAS_BASE/deploy (or under another
configuration-defined directory) and undeployed as soon as they has been
removed from this location.
Here is the part of jonas.properties concerning
the ear service:
###################### JOnAS EAR service configuration # # Set the name of the implementation class of the ear service. jonas.service.ear.class org.ow2.jonas.ear.internal.JOnASEARService # Set the XML deployment descriptors parsing mode for the EAR service # (with or without validation). jonas.service.ear.parsingwithvalidation true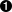
This service provides containers for EJB2.1 components.
An EJB container can be created from an ejb-jar file using one of the following
possibilities:
-
The
ejb-jarfile has been copied under $JONAS_BASE/deploy -
The
ejb-jarfile is packaged inside an ear file as a component of a Java EE application. The container will be created when the Java EE application will be deployed via the ear service. -
EJB containers may be dynamically created from ejb-jar files using the JonasAdmin tool.
-
EJB containers may be dynamically created from ejb-jar files using the command jonas admin:
jonas admin -a <some-dir>/sb.jar
The ejb service can (and by default does) provide monitoring options. Monitoring provides the following values at a per-EJB basis for stateful and stateless beans:
-
Number of calls done on all methods.
-
Total business time, i.e. the time spent executing business (applicative) code.
-
Total time, i.e. the total time spent executing code (business code + container code).
The warningThreshold option can be used to generate a warning each time a method takes more than warningThreshold milliseconds to execute. By default, warningThreshold is set to 20 seconds.
Here is the part of jonas.properties concerning
the ejb2 service:
###################### JOnAS EJB 2 Container service configuration # # Set the name of the implementation class of the ejb2 service jonas.service.ejb2.class org.ow2.jonas.ejb2.internal.JOnASEJBService # Set the XML deployment descriptors parsing mode (with or without validation) jonas.service.ejb2.parsingwithvalidation true # If enabled, the GenIC tool will be called if : # - JOnAS version of the ejb-jar is not the same version than the running JOnAS instance # - Stubs/Skels stored in the ejb-jar are not the same than the JOnAS current protocols. # By default, this is enabled jonas.service.ejb2.auto-genic true # Arguments for the auto GenIC (-invokecmd, -verbose, etc.) jonas.service.ejb2.auto-genic.args -invokecmd # Note: these two settings can be overriden by the EJB descriptor. # # If EJB monitoring is enabled, statistics about method call times will be # collected. This is a very lightweight measurement and should not have much # impact on performance. jonas.service.ejb2.monitoringEnabled true # If EJB monitoring is enabled, this value indicates after how many # milliseconds spent executing an EJB method a warning message should be # displayed. If 0, no warning will ever be displayed. jonas.service.ejb2.warningThreshold 20000
For customizing the ejb2 service it is possible to:
-
Set or not the XML validation at the deployment descriptor parsing time
-
Set or not the automatic generation via the GenIC tool
-
Specify the arguments to pass to the GenIC tool
The ejb3 service provides EJB 3 container support. This service is provided by the EasyBeans container.
The declaration of the ejb3 service is done in the
jonas.properties file.
###################### JOnAS EJB 3 container service configuration # # Set the name of the implementation class of the EJB 3 service. jonas.service.ejb3.class org.ow2.jonas.ejb.easybeans.EasyBeansService
EasyBeans has its
own configuration file that is located in JONAS_BASE/conf folder. The name of the
configuration file is easybeans-jonas.xml.
By default, EasyBeans is using only services provided by JOnAS. Thus, no additional components are required for starting EasyBeans.
<?xml version="1.0" encoding="UTF-8"?>
<easybeans xmlns="http://org.ow2.easybeans.server">
<!-- No infinite loop (managed by JOnAS): wait="false"
Enable MBeans: mbeans="true"
Disable the naming: naming="false"
Use JOnAS JACC provider: jacc="false"
Using JOnAS monitoring: scanning="false"
Using JOnAS JMX Connector: connector="false"
Disable Deployer and J2EEServer MBeans: deployer="false" & j2eeserver="false"
-->
<config
wait="false"
mbeans="true"
naming="false"
jacc="false"
scanning="false"
connector="false"
deployer="false"
j2eeserver="false" />
<!-- Define components that will be started at runtime -->
<components>
<!-- All components are launched by JOnAS -->
<!-- RMI component will be used to access some of JNDI properties -->
<!-- But as there are no protocols, no registry is launched. -->
<rmi />
<!-- Start smartclient server with a link to the rmi component-->
<!--smart-server port="2503" rmi="#rmi" /-->
</components>
</easybeans>
The <config> element describes EasyBeans configuration properties
that may be different for each application server. The settings provided in
this file are the JOnAS settings and they shouldn't be modified in almost
any cases.
The <component> element defines the
EasyBeans components
that will be started at the startup. Here EasyBeans is integrated in
JOnAS, it will thus
use JOnAS services like transaction, security, naming, registry.
The smart client component provides a mechanism for downloading classes missing on the client side, from the server side. This allows to have a very small library on the client side and it downloads classes on demand. When this component is enabled, the listening port can be configured. More documentation on the Smart component can be found in EasyBeans documentation.
The ha (High Availability) service is required in order to replicate stateful session beans (SFSBs).
The ha service uses JGroups as a group communication protocol (GCP).
Here is the part of jonas.properties related to
ha service:
###################### JOnAS HA service configuration # # Set the name of the implementation class of the HA service. jonas.service.ha.class org.ow2.jonas.ha.internal.HaServiceImpl # Set the JGroups configuration file name jonas.service.ha.jgroups.conf jgroups-ha.xml# Set the JGroups group name jonas.service.ha.jgroups.groupname jonas-rep
# Set the SFSB backup info timeout. The info stored in the backup node is removed when the timer expires. jonas.service.ha.gc.period 600
# Set the datasource for the tx table jonas.service.ha.datasource jdbc_1
# Reconnection timeout for JGroups Channel, if it's closed on request. jonas.service.ha.reconnection.timeout 5000
|
Set the name of the JGroups configuration file. |
|
|
Set the name of the JGroups group. |
|
|
Set the period of time (in seconds) the system waits before cleaning useless repliaction information. |
|
|
Set the JNDI name of the datasource corresponding to the database where is located the transaction table used by the replication mechanism. |
|
|
Set the delay to wait a reconnection. |
The jmx service is a mandatory service, so its automatically started in order to administrate or instrument the JOnAS server. It uses the JMX extensions provided by the current Java EE platform.
The jmx service creates at stratup, one or more JMX Remote connectors (one for each protocol configured in CAROL, seeSection 2.2, “Configuring the communication protocol and JNDI”). This allows remote management for JMX-based administration applications. A connector's address is based on the corresponding protocol's URL, the protocol name and the server name.
Let's consider the default CAROL configuration, where the RMI/JRMP protocol is used with the following URL:
carol.protocols=jrmp carol.jrmp.url=rmi://localhost:1099
The address of the JMX Remote connector for a server named myJonas is:
service:jmx:rmi:///jndi/rmi://localhost:1099/jrmpconnector_myJonas
The jmx service can be started in secured or non-secured mode:
-
In non-secured mode, the JOnAS server accepts JMX connections directly, without requiring the client to provide any credentials (no user names or passwords). This implies that any person that has access to the JOnAS server's JMX port (by default, its RMI/JRMP port) can also take any action on the server (including remote code execution).
-
In secured mode, any client that connects to the JOnAS server via JMX must provide a valid user name and password.
-
When connecting, the client provides a user name and password by setting the JMXConnector.CREDENTIALS key of the properties passed to the connection (env variable of the JMXConnector.connect method).
This user name and password is always directly transmitted to the JOnAS server the client is connecting to, and it's that server's decision whether:
-
The user name and password is considered as being valid, therefore the connection will be accepted. This phase is called Authentication .
-
That user has the right of accessing a certain method of a certain instance. This phase is called Authorization.
-
-
For authentication, you can use any JAAS LoginModule of the JMX extensions provided by your platform.
For authorization, you can use any Security Manager provided by your platform.
-
Here is the part of jonas.properties concerning
the jmx service:
###################### JOnAS JMX service configuration # # Set the name of the implementation class of the JMX service jonas.service.jmx.class org.ow2.jonas.jmx.internal.JOnASJMXService # Set to true if the JMXRemote interface should require the client to provide # authentication information. That information is provided when establishing # the JMX connection, using the JMXConnector.CREDENTIALS key. # # Note that if you enable JMX security for a server, all clients (including # any administration tool such as the domain master) connecting to this # instance via JMX must provide a valid user name and password. jonas.service.jmx.secured false # If jonas.service.jmx.secured is set to true, defines the authentication # method and the method's parameter. For example, to use file-based # authentication using the conf/jmx.passwords file, define: # jonas.service.jmx.authentication.method jmx.remote.x.password.file # jonas.service.jmx.authentication.parameter conf/jmx.passwords # You are free to use the authentication provider you wish. jonas.service.jmx.authentication.method jmx.remote.x.password.file jonas.service.jmx.authentication.parameter conf/jmx.passwords # You may for example choose to use JAAS LoginModule for authentication. # In this case define the used configuration in the JAAS configuration file # using the jonas.service.jmx.authentication.parameter: # jonas.service.jmx.authentication.method jmx.remote.x.login.config # jonas.service.jmx.authentication.parameter jaas-jmx # If jonas.service.jmx.secured is set to true, defines the authorization # method and the method's parameter. For example, to use file-based # authorization using the conf/jmx.access file, define: # jonas.service.jmx.authorization.method jmx.remote.x.access.file # jonas.service.jmx.authorization.parameter conf/jmx.access # You are free to use the authorization provider you wish. jonas.service.jmx.authorization.method jmx.remote.x.access.file jonas.service.jmx.authorization.parameter conf/jmx.access # You may for example choose to use role-based authorization manager # configured using conf/jmx.rolebased.access file. In this case, define: # jonas.service.jmx.authorization.method jmx.remote.x.access.rolebased.file # jonas.service.jmx.authorization.parameter conf/jmx.rolebased.access
The jtm service is used by ejb2 service in order to provide transaction management for EJB components as defined in the deployment descriptor. The jtm service uses a Transaction manager that may be local or may be launched in another JVM (a remote Transaction manager). Typically, when there are several JOnAS servers working together, one jtm service must be considered as the master and the others as slaves. The slaves must be configured as if they were working with a remote Transaction manager.
By default JOTM is the Transaction manager used.
Here is the part of jonas.properties concerning
the jtm service:
###################### JOnAS JTM Transaction service configuration # # Set the name of the implementation class of the jtm service jonas.service.jtm.class org.ow2.jonas.tm.jotm.JOTMTransactionService # Set the Transaction Manager launching mode. # If set to 'true', TM is remote: TM must be already launched in an other JVM. # If set to 'false', TM is local: TM is going to run into the same JVM # than the jonas Server. jonas.service.jtm.remote false # Set the default transaction timeout, in seconds. jonas.service.jtm.timeout 60
For customizing the jtm service It is possible to
-
Indicate if the Transaction Manager used in this instance is collocated or remote: jonas.service.jtm.remote property
-
Setting the value of the transaction time-out, in seconds: jonas.service.jtm.timeout property
The mail service is an optional service that may be used to send emails.
It is based on JavaMail and on JavaBeans Activation Framework (JAF) API.The default implementation of the mail service rely on the GNUMail implementation of these API.
A mail factory is required in order to send or receive mails. JOnAS
provides two types of mail factories:
javax.mail.Session and
javax.mail.internet.MimePartDataSource.
MimePartDataSource factories allow mail to be sent
with a subject and the recipients already set.
Mail factory objects must be configured according to their type. The
subsections that follow briefly describe how to configure
Session and MimePartDataSource
mail factory objects, in order to run the SessionMailer SessionBean and the
MimePartDSMailer SessionBean delivered with the platform.
Here is the part of jonas.properties concerning
the mail service:
###################### JOnAS Mail service configuration # # Set the name of the implementation class of the mail service jonas.service.mail.class org.ow2.jonas.mail.internal.JOnASMailService # Set the jonas mail factories. # This property is set with a coma-separated list of MailFactory properties # file names (without the '.properties' suffix). # Ex: MailSession1,MailMimePartDS1 (while the properties file names are # MailSession1.properties and MailMimePartDS1.properties) jonas.service.mail.factories
Mail factory objects created by JOnAS must be
given a name. For example, consider two factories called
MailSession1 and MailMimePartDS1. Each
factory must have a configuration file whose name is the name of the factory
with the .properties extension
(MailSession1.properties for the MailSession1
factory).
For this example jonas.service.mail.factories property must be set to:
jonas.service.mail.factories MailSession1,MailMimePartDS1
A template MailSession1.properties file is
supplied in $JONAS_BASE/conf. It
contains two mandatory properties :
#Factory Name/Type mail.factory.name mailSession_1 mail.factory.type javax.mail.Session
The JNDI name of the mail factory object is mailSession_1. This template must be updated with values appropriate to your installation. See the section "Configuring a mail factory" below for the list of available properties.
A template MimePartDS1.properties is supplied
in $JONAS_BASE/conf. It contains
two mandatory properties :
#Factory Name/Type mail.factory.name mailMimePartDS_1 mail.factory.type javax.mail.internet.MimePartDataSource
The JNDI name of the mail factory object is mailMimePartDS_1. This template must be updated with values appropriate to your installation. See the section "Configuring a mail factory" below for the list of available properties.
Here are the possible properties
-
Required properties:
| Property name | Description |
| mail.factory.name | JNDI name of the mail factory |
| mail.factory.type | The type of the factory. This property can be javax.mail.Session or javax.mail.internet.MimePartDataSource. |
-
Optional properties: Authentication properties
| Property name | Description |
| mail.authentication.username | Set the username for the authentication. |
| mail.authentication.password | Set the password for the authentication. |
-
Optional properties: javax.mail.Session.properties (refer to JavaMail documentation for more information)
| Property name | Description |
| mail.debug | The initial debug mode. Default is false. |
| mail.from | The return email address of the current user, used by the InternetAddress method getLocalAddress. |
| mail.mime.address.strict | The MimeMessage class uses the InternetAddress method parseHeader to parse headers in messages. This property controls the strict flag passed to the parseHeader method. The default is true. |
| mail.host | The default host name of the mail server for both Stores and Transports. Used if the mail.protocol.host property is not set. |
| mail.store.protocol | Specifies the default message access protocol. The Session method getStore() returns a Store object that implements this protocol. By default the first Store provider in the configuration files is returned. |
| mail.transport.protocol | Specifies the default message access protocol. The Session method getTransport() returns a Transport object that implements this protocol. By default, the first Transport provider in the configuration files is returned. |
| mail.user | The default user name to use when connecting to the mail server. Used if the mail.protocol.user property is not set. |
| mail.<protocol>.class | Specifies the fully- qualified class name of the provider for the specified protocol. Used in cases where more than one provider for a given protocol exists; this property can be used to specify which provider to use by default. The provider must still be listed in a configuration file. |
| mail.<protocol>.host | The host name of the mail server for the specified protocol. Overrides the mail.host property. |
| mail.<protocol>.port | The port number of the mail server for the specified protocol. If not specified, the protocol's default port number is used. |
| mail.<protocol>.user | The user name to use when connecting to mail servers using the specified protocol. Overrides the mail.user property. |
-
Optional properties:MimePartDataSource properties (Only used if mail.factory.type is javax.mail.internet.MimePartDataSource)
| Property name | Description |
| mail.to | Set the list of primary recipients ("to") of the message. |
| mail.cc | Set the list of Carbon Copy recipients ("cc") of the message. mail.bcc |
| mail.bcc | Set the list of Blind Carbon Copy recipients ("bcc") of the message. |
| mail.subject | Set the subject of the message. |
This service is used for accessing the RMI registry, CMI registry, or
the CosNaming (RMI/IIOP), depending on the configuration of communication
protocols specified in carol.properties, refer to Section 2.2, “Configuring the communication protocol and JNDI” .
Here is the part of jonas.properties file
concerning the registry service.
###################### JOnAS Registry service configuration # # Set the name of the implementation class of the Registry service jonas.service.registry.class org.ow2.jonas.registry.carol.CarolRegistryService # Set the Registry launching mode # If set to 'automatic', the registry is launched in the same JVM as Application Server, # if it's not already started. # If set to 'collocated', the registry is launched in the same JVM as Application Server # If set to 'remote', the registry has to be launched before in a separate JVM jonas.service.registry.mode collocated
The resource service must be started when Java EE components require access to an external Enterprise Information Systems. The standard way to do this is to use a third party software component called Resource Adapter.
The role of the Resource service is to deploy the Resource Adapters in the JOnAS server, i.e., configure it in the operational environment and register in JNDI name space a connection factory instance that can be looked up by the application components. The resource service implements the Java EE Connector Architecture 1.5[7].
Resource Adapter are packaged in Java EE rar archives.
In development mode, as all other Java EE archives rar archives can be deployed automatically as soon as they are copied under $JONAS_BASE/deploy and undeployed as soon as they has been removed from this location.
For more information see Section 2.4.3, “depmonitor service configuration”.
The other ways to deploy rar archives is
-
to use the jonasAdmin console.
-
to use the command jonas admin:
jonas admin -a <mydir>/myrar.rar
A JOnAS specific resource adapter configuration xml file must be included in each resource adapter. This file replicates the values of all configuration properties declared in the deployment descriptor for the resource adapter. Refer to Defining the JOnAS Connector Deployment Descriptor in J2EE Connector Programmer's Guide for additional information.
Here is the part of jonas.properties related to
resource service:
###################### JOnAS J2CA resource service configuration # # Set the name of the implementation class of the J2CA resource service jonas.service.resource.class org.ow2.jonas.resource.internal.JOnASResourceService
The worker thread pool used for all J2CA 1.5 Resource Adapters deployed can be configured in the Section 2.4.19, “wm service configuration” service.
resource service is mainly used in JOnAS for accessing databases via a JDBC resource adapter (in this case it replace dbm service) and for providing JMS facilities.
JOnAS provides several JDBC resource adapters and a JMS resource adapter on top of JORAM More information about configuring resource adapters can be found in Section 2.6, “Configuring JDBC Resource Adapters”
Here is the part of jonas.properties related to
security service:
# ###################### JOnAS SECURITY service configuration # # Set the name of the implementation class of the security service jonas.service.security.class org.ow2.jonas.security.internal.JonasSecurityServiceImpl # Realm used for CsiV2 authentication jonas.service.security.csiv2.realm memrlm_1 # Realm used for Web Service authentication jonas.service.security.ws.realm memrlm_1 # Registration of realm resources into JNDI # Disable by default so configuration is not available with clients jonas.service.security.realm.jndi.registration false # Enable security context check on Remote Login Module jonas.security.context.check false # Path to the keystore file jonas.security.context.check.keystoreFile /tmp/keystore # Pass used for the keystore file jonas.security.context.check.keystorePass keystorepass # Alias (stored in the keystore) jonas.security.context.check.alias FB
In fact properties
jonas.service.security.csiv2.realm and
jonas.service.security.ws.realm are only useful for
users that use security on top of rmi/iiop or on top of web services . in
these case with memrlm_1 it is possible to make a link to
the memomyrealm named memrlm_1 in the
$JONAS_BASE/conf/jonas-realm.xml file and retrieve
users name and roles.
Don't forget that for using security the global property jonas.security.propagation to true and that an important property related to security is jonas.security.manager see Section 2.1.4.1, “Global properties of jonas.properties”
All other security configuration related to JOnAS is done in the file jonas-realm.xml
and security configuration related to web containers,
certificate, etc., is done in the appropriate files. Refer to the subsection
Section 2.5, “Configuring Security” for a complete description of security
configuration.
This service has been designed for dynamic redeployment of applications, without any application downtime and without users' sessions being lost:
-
Deployment of a new version of an application does not require the undeployment of any previous version.
-
Users that were on a previous version keep on using that version as long as their session on that version is active (for example, as long as they have not finished buying items on the previous version of the online trade web site). This guarantees that no user data will be lost, and that if there is any problem with the new version the old version is still available instantly.
-
New versions of the application can be deployed using various strategies, for instance allow testing of the new version by a small community to ensure its readiness for production.
The versioning service achieves this by adding virtual contexts to all services that provide support for versioning. To use the versioning service:
-
Enable the versioning service in
jonas.properties -
Define the Implementation-Version attribute in your deployable file's (whether
war,jarorear)MANIFEST. Note that:-
ANT, Maven as well as most IDEs can set any
MANIFESTattribute automatically. -
If the archive that will be deployed is an
ear, the Implementation-Version defined in theMANIFESTof the ear will be used for all archives theearcontains.
-
When the versioning service is enabled, application resources (web pages, EJBs, etc.) are accessed the following way:
-
Each versioned application has a user (virtual) address. Each version of an application is renamed and bound to that virtual address. Each bound version has a policy (that can be changed in time in order to manage the deployment strategy):
-
Private: Can only be accessed by clients that satisfy some prerequisites; for example belong to a certain IP address group or provide a certain credential.
-
Reserved: Not accessible using the virtual address, therefore can only be accessed directly (using the versioned address).
-
Disabled: Only accessible by clients that have been using this version in the past (until their session expires). This guarantees that users will not lose their session data during a redeployment.
-
Default: Version accessed by all clients that don't fit in any other policy.
-
-
A user can access the application resource indirectly (using the virtual address) or directly (using the versioned address).
-
If the user tries to access the application resource indirectly (using the virtual address), the versioning system:
-
First checks if that user is defined as a user that can access a version of the application with the Private access policy. If that is the case, the user is routed to that private version of the application.
-
Then checks if that user already has a session in a version of the application with the Disabled access policy. If that is the case, the user is routed to that disabled version of the application.
-
If neither of these cases are true, routes the user to the version of the application with the Default access policy. If the application does not define any default version, the user will see "resource not found" message.
-
This can be schematized as follows:
 |
The current limitations of the versioning service are:
-
Only the Tomcat Web Container supports the versioning service. That support is fully functional, recognition of users is based on the session ID (via cookie or GET), but the Private context policy has not been implemented.
-
Both EJB2 and EJB3s support the versioning service. That support is fully functional, EJB lookups in the same EAR always redirect to the same version, but the Private context policy has not been implemented.
-
Web Service support for the versioning service is in design phase
As this service allows seamless and interruptionless upgrade and test
of all applications, it is strongly recommended for all applications to
refer version identifiers in their manifest files. Remember that ANT, Maven
as well as most IDEs can set any MANIFEST attribute
automatically.
We will now detail the way versioning works by creating two versions
of the Java EE 5 Sample Application in the
JOnAS examples
folder: version 1.0.0 and version 1.0.1. Since the application is an EAR, we
only need to refer the version identifier in the EAR file.
When the first version of the EAR is deployed:
-
The application gets deployed on the URI /javaee5-earsample-version1.0.0.
-
The virtual URI /javaee5-earsample is created.
-
The real URI /javaee5-earsample-version1.0.0 gets bound to the virtual URI /javaee5-earsample.
Therefore, when a user accesses the /javaee5-earsample URI, the content seen is the same as the one on /javaee5-earsample-version1.0.0.
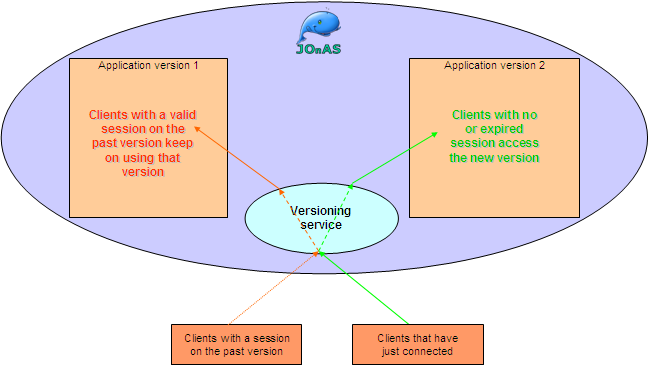
We now deploy the second version of the application, version 1.0.1, via the JOnAS Web Admin panel. When the second version is deployed, it is bound to the virtual URI as Reserved (this is the default policy and can be modified via JMX at any time). This means that the only way of accessing the 1.0.1 version of the application is to type as URI /javaee5-earsample-version1.0.1. All visitors of /javaee5-earsample will still access the version 1.0.0.
 |
To change the access policies of each version of the virtual URI (the only URI end users are expected to access), go to the list of Web Containers in the JOnAS Web Admin panel. If you set the version 1.0.0 as Disabled and the version 1.0.1 as Default:
-
The user that was on /javaee5-earsample when the default version was 1.0.0 will stay on version 1.0.0 until her/his session expires (i.e. the browser window is closed).
-
Any user that connects to /javaee5-earsample for the first time will visit version 1.0.1.
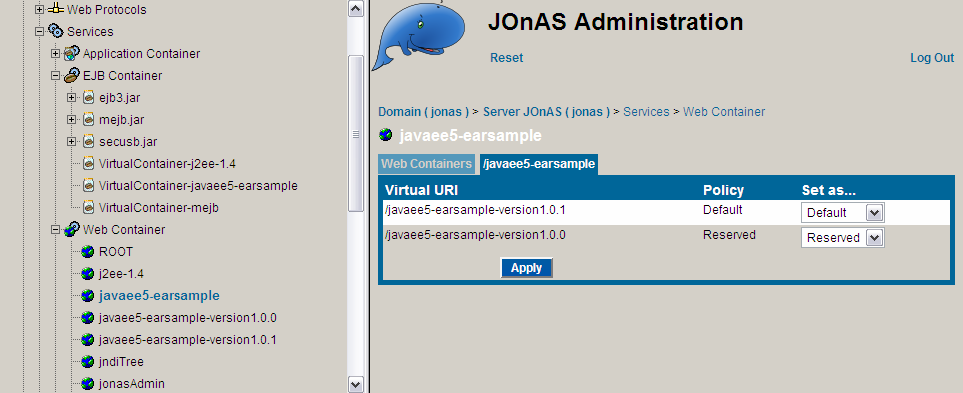
When the first version of the EAR is deployed:
-
All EJBs that register on the JNDI directory register with a prefixed name, which is their original name prefixed by javaee5_earsample_version1.0.0/. For example, the myStateless bean gets registered as javaee5_earsample_version1.0.0/myStateless.
-
For each EJB, the original JNDI name is also registered and points exactly to the same JNDI link.
Therefore, when a user looks up for the myStateless bean, the reference received is the same as the one received when javaee5_earsample_version1.0.0/myStateless is looked up.
The behaviours of the Web and EJB services when the version 1.0.1 is deployed are similar, except for one very important point: when multiple applications are packaged together, the only versions of the applications they've been tested against are the versions inside the same EAR. Therefore, blindly accessing the Default version of the EJBs could have unexpected results. This is why the concept of versioned EJB clients has been created:
-
All EJB clients in a versioned EAR automatically become versioned EJB clients. Their target version is the version of the host EAR, which implies that intra-EAR accesses are always done to the same version.
-
External EJB clients can also specify the versions for the EJB they need to access.
-
Non-versioned external EJB clients will access the Private, Reserved, Disabled or Default versions as usual.
This can be schematized as follows:
 |
As with the versioned Web Applications, to change the access policies of each version of the virtual JNDI container (which knows the JNDI names end users are expected to access), go to the list of EJB Containers in the JOnAS Web Admin panel. If you set the version 1.0.0 as Disabled and the version 1.0.1 as Default:
-
All clients that know about the versioned JNDI names (remember that this will always be the case in a versioned EAR application) will always access the version they specify.
-
References to myStateless obtained before this operation will stay on version 1.0.0.
-
Any user that looks up myStateless for the first time will get a reference to version 1.0.1.
The wc service allows to clean up periodically the work directory of the JOnAS server.
During the deployment process of an application, a specific working directory is created and associated to the application. After a defined time, the clean task tries to delete working directories of applications which have been undeployed. Note that the clean task is already executed at startup of the JOnAS server.
Here is the part of jonas.properties concerning
the wc service:
###################### JOnAS WorkCleaner service configuration # # Set the name of the implementation class of the wc service jonas.service.wc.class org.ow2.jonas.workcleaner.internal.JOnASWorkCleanerService # Set the clean period in seconds jonas.service.wc.period 300
This service provides containers for the web components used by the Java EE applications.
JOnAS
provides two implementations of this service: one for Jetty 6.x, one for
Tomcat 6.x. It is necessary to run this service in order to use the
JonasAdmin tool. A web container is created from a war file.
In development mode, as all other Java EE archives war archives can be deployed automatically as soon as they are copied under $JONAS_BASE/deploy and undeployed as soon as they has been removed from this location.
Here is the part of jonas.properties concerning
the web service:
###################### JOnAS Web container service configuration # # Set the name of the implementation class of the web container service. jonas.service.web.class org.ow2.jonas.web.tomcat6.Tomcat6Service #jonas.service.web.class org.ow2.jonas.web.jetty6.Jetty6Service # Set the XML deployment descriptors parsing mode for the WEB container # service (with or without validation). jonas.service.web.parsingwithvalidation true
For customizing the web service It is possible to
-
Set or not the XML validation at the deployment descriptor parsing time
The wm service provides a J2CA WorkManager implementation.
Here is the part of jonas.properties concerning
the wm service:
###################### JOnAS WorkManager service configuration # # Set the name of the implementation class of the wm service jonas.service.wm.class org.ow2.jonas.workmanager.internal.JOnASWorkManagerService # Set the size of the worker thread pool jonas.service.wm.minworkthreads 3# Set the maximun size of the worker thread pool jonas.service.wm.maxworkthreads 80
# Set the max # of seconds that a thread will wait for work # This is used to shrink the worker thread pool back to minimum jonas.service.wm.threadwaittimeout 60

|
Defines the minimum size of the Thread pool |
|
|
Defines the maximum size of the Thread pool |
|
|
Defines the maximum time (in seconds) that a worker Thread should wait before execution |
The wm service is used, for example,
in the resource service (J2CA 1.5
implementation) in order to provide a
javax.resource.spi.work.WorkManager instance for
deployed resource adapters (like JMS, ...).
The ws service use the Axis 1.x implementation.
Here is the part of jonas.properties concerning
the ws service:
###################### JOnAS WebServices service configuration # # Set the name of the implementation class of the WebServices service. jonas.service.ws.class org.ow2.jonas.ws.axis.AxisService # Set the JServiceFactory to use jonas.service.ws.factory.class org.ow2.jonas.ws.axis.JAxisServiceFactory # Set the XML deployment descriptors parsing mode for the WebServices # service (with or without validation). jonas.service.ws.parsingwithvalidation true # Set the WSDL Handler list for WSDL publication # A minimum of 1 WSDLHandler is required ! # This property is set with a coma-separated list of WSDLHandler properties # file names (without the '.properties' suffix). # Ex: file1,uddi (while the properties file names are # file1.properties and uddi.properties) jonas.service.ws.wsdlhandlers file1 # Set the Generator to use with wsgen jonas.service.ws.wsgen.generator.factory org.ow2.jonas.generators.wsgen.generator.ews.EWSGeneratorFactory # Set the prefix that will be used to compute URL endpoints for web services # Example of prefix: http://www.mydomain.com:8888 jonas.service.ws.url-prefix # Set automatic WsGen mode on/off # If set to 'true', WsGen will automatically be applied to all deployed archives (EjbJars, Webapps, Applications) jonas.service.ws.auto-wsgen.engaged true
or customizing the ws service It is possible to :
-
Set or not the XML validation at the deployment descriptor parsing time: property jonas.service.ws.parsingwithvalidation
-
Choose one or more WSDL Handler(s): property jonas.service.ws.wsdlhandlers
WSDL Handlers are used to locate and publish all WSDL documents. WSDL handlers are configured in WSDLHandler properties.
-
Enforce the URL to be used for the deployed endpoints: property:jonas.service.ws.url-prefix
This is interesting when there is a cluster of JOnAS instances and a unique HTTP frontend for load balancing. For example the administrator wants all your web services endpoint to use the
http://www.mywebserver.comURL instead of the usualhttp://localhost:9000(that has a meaning only at local level). -
Enable or not to run the WSGen tool on ejb-jar, war, ear and application client at deployment time.
The File WSDLHandler type is used in simple WebServices usage scenario, when the application doesn't requires a full blown web services registry (like UDDI or ebXML). It will simply save the WSDL documents (and their dependencies) in a configurable directory.
# FileWSDLHandler class jonas.service.wsdl.class org.ow2.jonas.ws.base.handler.FileWSDLHandler # Directory where WSDLs will be copied # If not set JONAS_BASE/wsdls will be used # jonas.service.publish.file.directory /tmp# Encoding of the file (In respect with the platform JOnAS is running on) # If not set default to UTF-8 jonas.service.publish.file.encoding UTF-8
The JAXR WSDLHandler is a WSDL Handler responsible of publishing the application WSDL in an enterprise level registry or repository, allowing external clients to get the technical and administrative information about the deployed service.[8]
# RegistryWSDLHandler class jonas.service.wsdl.class org.ow2.jonas.ws.base.handler.RegistryWSDLHandler # User name and Password to access Registry jonas.service.publish.uddi.username jonasjonas.service.publish.uddi.password jonas
# Organization name, small desc (optionnal) and primary contact name. jonas.service.publish.uddi.organization.name OW2
jonas.service.publish.uddi.organization.desc OW2 Consortium (http://www.objectweb.org)
jonas.service.publish.uddi.organization.person_name JOnAS
# URLs where Registry can be contacted (Publish an Query APIs) javax.xml.registry.lifeCycleManagerURL http://localhost:9000/juddi/publish
javax.xml.registry.queryManagerURL http://localhost:9000/juddi/inquiry

The security service is used by the ejb, web, ws services to provide security for Java EE components. The ejb service provides security in two forms: declarative security and programmatic security that is described in the EJB Programmer's Guide: Security Management .
The security service exploits security roles and method permissions located in the Java EE deployment descriptors.
A main concept in security is Authentication which is the mechanism telling the container the identity of the user making the current request.
A caller is a client that may be a servlet client or a container client. Usually a client proves its identity by a couple user/password or a certificate (credential). Once the identification is correct JOnAS must build a security context that will be propagated with requests and be used by the container to verify that the user exists and has permissions sufficient to make the request.
JAAS is a standard framework for authenticating users. It defines
configuration files (jaas.config) and interfaces like
the LoginModule interface that may be used in
JOnAS to
perform authentication tasks.
Lightweight authentication mechanism using JACC may be used to authenticate servlet client.
In the Tomcat documentation we can find this definition: “A Realm is a "database" of usernames and passwords that identify valid users of a web application (or set of web applications), plus an enum eration of the list of roles associated with each valid user.”
In both authentication mechanisms the container use a realm
to verify validity of users. In JOnAS the
realm may be a database accessed via JDBC (Database
realm), a LDAP directory (LDAP realm) or a flat file (Memory realm). The
type of realm to use is specified in
$JONAS_BASE/conf/jonas-realm.xml.
The file $JONAS_BASE/conf/jonas-realm.xml file
describes:
-
the content of flat file memory realm
-
how to access a database realm
-
how to access a LDAP realm
The memoryrealm must be named and defines users, groups and roles in the section <jonas-memoryrealm>
<jonas-memoryrealm> <memoryrealm name="memrlm_1"><roles> <role name="jonas-admin" description="JonasAdmin role" />
<role name="tomcat" description="Used in examples" /> </roles> <groups> <group name="jonas" roles="jonas-admin,tomcat,jaas,ws-security" description="All authorization" />
</groups> <users> <user name="tomcat" password="tomcat" roles="tomcat,jonas-admin,manager" />
<user name="jetty" password="jetty" roles="jetty" /> <!-- Example of a crypt password : password for jadmin is : jonas --> <user name="jadmin" password="{MD5}nF3dVBB3NPfRgzWlJFwoaw==" roles="jonas-admin" />
<user name="jps_admin" password="admin" roles="administrator" /> <user name="supplier" password="supplier" roles="administrator" /> <!-- Another crypt example in another format : password is jonas --> <!-- JonasAdmin uses name="jonas" password="jonas" --> <user name="jonas" password="SHA:NaLG+uYfgHeqth+qQBlyKr8FCTw=" groups="jonas" />
<user name="principal1" password="password1" roles="role1" /> <user name="principal2" password="password2" roles="role2" /> </users> </memoryrealm> </jonas-memoryrealm>
|
memoryrealm must be named. This name will be used in the web container configuration file |
|
|
definition of a security role |
|
|
definition of a group of roles |
|
|
definition of a user with non encrypted password and a list of roles |
|
|
definition of a user with encrypted password (format MD5) |
|
|
definition of a user with encrypted password (format SHA) |
Users, groups, and roles information are stored in a database; the configuration for accessing the corresponding database is described in the section <jonas-dsrealm>
The configuration requires the name of a datasource, the tables used, and the names of the columns.
<jonas-dsrealm> <dsrealm name="dsrlm_1"dsName="jdbc_1"
userTable="realm_users" userTableUsernameCol="user_name" userTablePasswordCol="user_pass"
roleTable="realm_roles" roleTableUsernameCol="user_name" roleTableRolenameCol="role_name">
</dsrealm> </jonas-dsrealm>
|
dsrealm must be named |
|
|
JNDI name of the |
|
|
defines the name of the user table and the name of the columns for username/password |
|
|
defines the name of the role table and the name of the columns for username/rolename |
to use this database a Datasource
configuration with the right JNDI name for the dbm
service must be set in the jonas.properties
file.
Users, groups, and roles information are stored in an LDAP directory. This is described in the section <jonas-ldaprealm>
There are some optional parameters. If they are not specified,
some of the parameters are set to a default value. For example if the
providerUrl element is not set, the default value is
ldap://localhost:389. The jonas-realm_1_0.dtd
DTD file show the default values.
Depending on the servlet container used, configuration differs.
-
Tomcat configuration:
Tomcat embedded in the JOnAS distribution is configured in
$JONAS_BASE/conf/server.xmlto use the memory realm namedmemrlm_1<Server> [...] <Realm className="org.objectweb.jonas.security.realm.web.catalina55.JACC" resourceName="memrlm_1" /> [...] </Server>
The authentication mechanism implemented by the class
org.objectweb.jonas.security.realm.web.catalina55.JACCis able to work with database or LDAP realm configured injonas-realm.xml.The value of resourceName attribute identifies the realm to be used injonas-realm.xml. -
webapp configuration:
In the
web.xmlof the web application a basic autjentication or a Form based authentication may be used<web-app> <login-config> <auth-method>BASIC</auth-method> <realm-name>Example Basic Authentication Area</realm-name> </login-config> </web-app>or
<web-app> <login-config> <auth-method>FORM</auth-method> <form-login-config> <form-login-page>login.jsp</form-login-page> <form-error-page>error.jsp</form-error-page> </form-login-config> </login-config> </web-app>
Like basic authentication, form-based authentication is not secure, since the content of the user dialog is sent as plain text, and the target server is not authenticated.
To overcome this vulnerability the authentication protocol may be run over a SSL session that ensures that all message contents are protected for confidentiality.
In this case, users will not have to enter a login/password. They will just present their certificates and authentication is performed transparently by the browser (after the user has imported his certificate into it). Therefore, the identity presented to the server is not a login, but a Distinguished Name(DN).
-
The name identifying the person to whom the certificate belongs looks like the following: CN=Someone Unknown, OU=ObjectWeb, O=JOnAS, C=ORG with:
CN : Common Name
OU : Organizational Unit
O : Organization
C : Country Name
E : Email Address
L : Locality
ST :State or Province Name
The Subject in a certificate contains the main attributes and may include additional ones, such as Title, Street Address, Postal Code, Phone Number.
In the jonas-realm.xml a user with password looks like:
<user name="jps_admin" password="admin" roles="administrator"/>
A certificate-based user must have its DN preceded by the String: ##DN## example:
<user name="##DN##CN=whale, OU=ObjectWeb, O=JOnAS, L=JOnAS, ST=JOnAS, C=ORG" password="" roles="jadmin" /> -
Tomcat Realm configuration:
The current Realm in $JONAS_BASE/conf/server.xml must be replaced by:
<Server> [...] <Realm className="org.objectweb.jonas.security.realm.web.catalina55.JAAS" /> [...] </Server>
The class specified uses the JAAS model to authenticate the users. Thus, to choose the correct realm to be used for authentication, JAAS must be configured see in Section 2.5.4, “JAAS configuration”.
-
Tomcat SSL configuration:
The following example of <connector> element must be uncommented in $JONAS_BASE/conf/server.xml and customized (if necessary):
<Server> [...] <!-- Define a SSL Coyote HTTP/1.1 Connector on port 9043 --> <!-- <Connector port="9043" maxHttpHeaderSize="8192" maxThreads="150" minSpareThreads="25" maxSpareThreads="75" enableLookups="false" disableUploadTimeout="true" acceptCount="100" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" /> --> [...] </Server>A complete description of SSL configuration can be found in SSL Configuration HOW-TO
-
Webapp configuration:
In the
web.xmlof the web application a Client Certificate Authentication Configuration must be set, a security-constraint may be used if needed; example:<web-app> <login-config> <auth-method>CLIENT-CERT</auth-method> <realm-name>Example Authentication Area</realm-name> </login-config> <security-constraint> .. <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint> </web-app>
-
Jetty configuration
A web-jetty.xml file must be provided in the
WEB-INFdirectory in the.warfile in which a security interceptororg.objectweb.jonas.security.realm.web.jetty50.Standardform is specified instead of the default one:<Configure class="org.mortbay.jetty.servlet.WebApplicationContext"> <Call name="setRealmName"> <Arg>Example Basic Authentication Area</Arg> </Call> <Call name="setRealm"> <Arg> <New class="org.objectweb.jonas.security.realm.web.jetty50.Standard"> <Arg>Example Basic Authentication Area</Arg> <Arg>memrlm_1</Arg> </New> </Arg> </Call> </Configure>Several
web-jetty.xmlexamples are located in the$JONAS_ROOT/examples/earsampleexample and$JONAS_ROOT/examples/alarmdemo. -
webapp configuration:
is similar to the webapp configuration with Tomcat see ???.
-
Jetty Realm configuration:
Edit the web-jetty.xml file under WEB-INF directory in the .war file to declare a Realm name and a Realm:
<Configure class="org.mortbay.jetty.servlet.WebApplicationContext"> ... !-- Set the same realm name as the one specified in <realm-name> in <login-config> in the web.xml file of your web application --> <Call name="setRealmName"> <Arg>Example Authentication Area</Arg> </Call> <!-- Set the class Jetty has to use to authenticate the user and a title name for the pop-up window --> <Call name="setRealm"> <Arg> <New class="org.objectweb.jonas.security.realm.web.jetty50.JAAS"> <Arg>JAAS on Jetty</Arg> </New> </Arg> </Call> ... </Configure>The class specified uses the JAAS model to authenticate the users. Thus, to choose the correct realm to be used for authentication, JAAS must be configured, see in Section 2.5.4, “JAAS configuration”.
-
Jetty SSL configuration:
In the global deployment descriptor of Jetty (the jetty5.xml file), located in the $JONAS_BASE/conf directory, uncomment this part:
<!-- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - --> <!-- Add a HTTPS SSL listener on port 9043 --> <!-- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - --> <!-- UNCOMMENT TO ACTIVATE <Call name="addListener"> <Arg> <New class="org.mortbay.http.SunJsseListener"> <Set name="Port">9043</Set> <Set name="MinThreads">5</Set> <Set name="MaxThreads">100</Set> <Set name="MaxIdleTimeMs">30000</Set> <Set name="LowResourcePersistTimeMs">2000</Set> <Set name="Keystore"><SystemProperty name="jetty.home" default="."/>/etc/demokeystore</Set> <Set name="Password">OBF:1vny1zlo1x8e1vnw1vn61x8g1zlu1vn4</Set> <Set name="KeyPassword">OBF:1u2u1wml1z7s1z7a1wnl1u2g</Set> </New> </Arg> </Call> -->A complete description of howto configure SSL for Jetty may be founf here
-
webapp configuration
is similar to the webapp configuration with Tomcat see ???
-
jonas-realm configuration
is similar to the configuration with Tomcat see ???
To enable authentication mechanism in a client container it is necessary to
-
choose a callback handler
Callback handlers are responsible to get the user identity and to store it.
The choice of the callback handler is done in the
application-xmlfile, for example:<application-client> <callback-handler>org.objectweb.jonas.security.auth.callback.LoginCallbackHandler</callback-handler> </application-client>
JOnAS provides several callback handlers[9]:
-
LoginCallbackHandler: it is a text based handler that gets the user and password via stdin -
DialogCallbackHandler:handler using a Swing dialog window to query user and password -
NoInputCallbackHandler: is responsible to store a user/password -
CertificateCallback: is responsible to store a certificate
-
-
configure JASS for setting the LoginModules to be used to perform authentication see Section 2.5.4, “JAAS configuration”
In the $JONAS_ROOT/examples/jaasclient directory can
be found three examples of container clients using JAAS authentication as
well as one java client without container client that uses also
JAAS.
The JAAS configuration is made via the JAAS Login Configuration File
A login configuration file consists of one or more entries, each specifying which underlying authentication technology should be used for a particular application or applications.
The contents of the JAAS configuration file has the structure below:
Application_1 {
LoginModuleClassA Flag Options;
LoginModuleClassB Flag Options;
LoginModuleClassC Flag Options;
};
Application_2 {
LoginModuleClassB Flag Options;
LoginModuleClassC Flag Options;
};
Other {
LoginModuleClassC Flag Options;
LoginModuleClassA Flag Options;
};
There is a flag associated with all the LoginModules to configure their behaviour in case of success or failure:
-
required - The LoginModule is required to succeed. If it succeeds or fails, authentication still proceeds through the LoginModule list.
-
requisite - The LoginModule is required to succeed. If it succeeds, authentication continues through the LoginModule list. If it fails, control immediately returns to the application (authentication does not proceed through the LoginModule list).
-
sufficient - The LoginModule is not required to succeed. If it does succeed, control immediately returns to the application (authentication does not proceed through the LoginModule list). If it fails, authentication continues through the LoginModule list.
-
optional - The LoginModule is not required to succeed. If it succeeds or fails, authentication still proceeds through the LoginModule list.
JOnAS provides in
$JONAS_BASE/conf/jaas.config a JAAS Login
Configuration File already configured with some login
configuration.
There are two requirements: the entry dedicated to Tomcat must be named tomcat, and the entry for Jetty, jetty. Note that everything in this file is case-sensitive.
The predifined entries are:
-
tomcat used for authentication with the web container Tomcat
-
jetty used for authentication with the web container Jetty
-
jaasclient used when running
$JONAS_ROOT/examples/jaasclientexamples
The default configuration for the web container Tomcat is the following:
tomcat {
org.objectweb.jonas.security.auth.spi.JResourceLoginModule required
resourceName="memrlm_1"
;
};
this indicates that the
JResourceLoginModule Login Module must be used on
the memory realm named memrlm_1.
The default configuration for the web container Jetty is the same than the previous:
jetty {
org.objectweb.jonas.security.auth.spi.JResourceLoginModule required
resourceName="memrlm_1"
;
};
the configuration for the container clients examples :
jaasclient {
// Login Module to use for the example jaasclient.
org.objectweb.jonas.security.auth.spi.JResourceLoginModule required
resourceName="memrlm_1"
org.objectweb.jonas.security.auth.spi.ClientLoginModule required
globalCtx="true"
;
};
Here two Login Modules are used, one for checking the identity in the memoty realm, the second for propagating a security context with the client request.
To change the location and name of the
jaas.config file, edit the
$JONAS_BASE/bin/jonas.sh script and modify the
following line:
-Djava.security.auth.login.config=$JONAS_BASE/conf/jaas.config
JOnAS provides some predefined LoginModules:
- JResourceLoginModule
-
This is the main LoginModule. It is highly recommended that this one be used in every authentication, as it checks the user authentication information in the specified realm database, LDAP or memory.
This LoginModule delegates the authentication to the server . Here are the possible attributes to set:
attribute name description resourceName name of the realm serverName name of JOnAS instance (default value= jonas) useUpperCaseUsername if true Convert the username into uppercase for the authentication (default value=false) certCallback if true use certificate callback - CRLLoginModule
-
This LoginModule contains authentication based on certificates. However, when enabled, it will also permit non-certificate based accesses. It verifies that the certificate presented by the user has not been revoked by the Certification Authority that signed it. To use it, the directory in which to store the revocation lists (CRLs) files or an LDAP repository must exist.
attribute name description CRLsResourceName specifies how the CRLs are stored:Two possible values "Directory" or "LDAP" CRLsDirectoryName The directory containing the CRL files (the extension for these files must be .crl).address address of the server that hosts the LDAP repository port port used by the LDAP repository; CRLs are retrieved from an LDAP directory using the LDAP schema defined in RFC 2587 - SignLoginModule
-
login module that signs the current Subject ,. Here are the possible attributes to set:
attribute name description keystoreFile Name of the key store keystorePass password for the keystore keyPass password for the private key alias alias - ClientLoginModule
-
login module used for propagating the Principal and roles to the server, it doesn't make any authentication. This login module must be used when authentication for a client container. Here is the possible attribute to set:
attribute name description globalCtx if true set the security context for all the threads of the client container instead of only on the current thread. Useful for swing client. (default value= false)
Connection of an J2EE application to databases is done through JDBC Resource Adapters (JDBC RA).
Such Resource Adapters are deployed via the resource service as seen in Section 2.4.14, “resource service configuration”.
For both container-managed or bean-managed persistence, the JDBC Resource Adapter makes use of relational storage systems through the JDBC interface.
JDBC connections are obtained from a JDBC RA.
The JDBC RA implements the J2EE Connector Specification using the DataSource interface as defined in the JDBC standard extensions.
An JDBC RA is configured to identify a database and a means to access
it via a JDBC driver. Multiple JDBC RAs can be deployed either via the
jonas.properties file or included in the autoload directory of the resource service.
The following section explains how JDBC RARs can be defined and configured in the JOnAS server.
To support distributed transactions, the JDBC RA requires the use of at least a JDBC2-XA-compliant driver. Such drivers implementing the XADataSource interface are not always available for all relational databases. The JDBC RA provides a generic driver-wrapper that emulates the XADataSource interface on a regular JDBC driver. It is important to note that this driver-wrapper does not ensure a real two-phase commit for distributed database transactions.
The generic JDBC RAs of JOnAS provide implementations of the
java.sql.Driver,
javax.sql.DataSource,
javax.sql.ConnectionPoolDataSource,
and javax.sql.XADataSource interfaces. They are
located in the $JONAS_ROOT/rars/autoload directory and thus
are deployed automatically.They consist of base (or generic) RAs
facilitating the build of the user JDBC RAs.
Depending on the relational database management server and the available interface in the used JDBC-compliant driver, the user JDBC RA is linked (through the RAR link feature) to a generic RA (for example, the Driver's one). In this case, the user RA contains only a jonas-ra.xml file with some specific parameters, such as the connection url, the user/password, or the JDBC-Driver class.
| Resource adapter provided with JOnAS | description | jndi name |
| rars/autoload/JOnAS_jdbcDS.rar | Generic JDBC RA that implements the
DataSource interface |
JOnASJDBC_DS |
| rars/autoload/JOnAS_jdbcDM.rar | Generic JDBC RA that implements the
Driver interface |
JOnASJDBC_DM |
| rars/autoload/JOnAS_jdbcCP.rar | Generic JDBC RA that implements the
ConnectionPoolDataSource
interface |
JOnASJDBC_CP |
| rars/autoload/JOnAS_jdbcXA.rar | Generic resource adapter that implements the
XADataSource interface |
JOnASJDBC_XA |
The remainder of this section, which describes how to define and configure JDBC RAs, is specific to JOnAS. However, the way to use these JDBC RAs in the Application Component methods is standard, i.e., via the resource manager connection factory references (refer to the example in the section Writing Database Access Operations.
An RAR file must be deployed as explained in Section 2.4.14, “resource service configuration”.
Usually a resource Adapter contains in its rar file all the classes needed to access to
the external resource. In the case of a specific JDBC RA it contains only
a JOnAS specific deployment descriptor jonas-ra.xml
that tell what sort of generic resource adapter to use and information
related to the specific database used. The jar file of the actual JDBC driver mut be
copied in the right place to be seen by the JOnAS classloader : $JONAS_BASE/lib/commons.
Changing the configuration of the RA requires extracting and editing the deployment descriptor and updating the archive file. There are several possible ways to do this:
-
With the RAConfig command (refer to the JOnAS Commands Reference Guide for a complete description of the command).
-
Through the jonasAdmin console (refer to Administration guide for a complete description). In the jonasAdmin's tree, the Resource Adapter Module node (under the deployment node) contains a configure tab that allows editing of both the ra.xml file and the jonas-ra.xml file of the undeployed RA.
The jonas-ra.xml contains JOnAS specific information describing deployment information, logging, pooling, jdbc connections, and RAR config property values:
-
Deployment Tags:
-
Logging Tags:
property name description possible values log-enabled determines if logging should be enabled for the RAR. -
False (default value)
-
True
log-topic: defines the log topic that will be used to write log messages for this rar file. -
Any topic name
-
Default value is org.objectweb.jonas.jca
-
-
Pooling Tags
property name description possible values pool-init Initial size of the managed connection pool -
0 (default value)
-
n
pool-min Minimum size of the managed connection pool. -
0 (default value)
-
n
pool-max Maximum size of the managed connection pool. -
n
-
-1 = unlimited (default value)
pool-max-age-minutes Maximum number of minutes to keep the managed connection in the pool. -
0 = an unlimited amount of time.
-
n in minutes
pstmt-max Maximum number of PreparedStatements per managed connection in the pool. Only needed with the JDBC RA of JOnAS or another database vendor's RAR. Value of 0 is unlimited and -1 disables the cache. -
0 = unlimited
-
n (default value = 10)
-
-1 = cache disabled
pool-max-opentime Identifies the maximum number of minutes that a managed connection can be left busy. -
0 = an unlimited amount of time (default value).
-
n in minutes
pool-max-waiters: identifies the maximum number of waiters for a managed connection. Default value is 0. -
0 (default value)
-
n
pool-max-waittime identifies the maximum number of seconds that a waiter will wait for a managed connection. Default value is 0. -
0 (default value)
-
n in seconds
pool-sampling-period: identifies the number of seconds that will occur between statistics samplings of the pool. Default is 30 seconds. -
n in seconds (default value = 30s)
-
-
JDBC Connection Tags:
![[Note]](../../resources/images/note.png)
Note Only valid for Connection implementation of java.sql.Connection.
property name description possible values jdbc-check-level Level of checking that will be done for the jdbc connection. -
0 : no check (default value)
-
1: check connection still open
-
2 : send the test statement before reusing a connection from the pool
-
3: (keep-alive feature) send the test statement on each connection every pool-sampling-period
jdbc-test-statement Test SQL statement sent on the connection if the jdbc-check-level is greater than 1. -
A SQL statement
-
-
Config Property Value Tags:
Each entry must correspond to the config-property specified in the ra.xml of the RAR file. The default values specified in the ra.xml will be loaded first and any values set in the jonas-ra.xml will override the specified defaults. These tags differs dependiing on the generic JDBC RA used
property name description possible values dsClass Name of the class implementing java.sql.Driver,javax.sql.DataSource,javax.sql.ConnectionPoolDataSource, orjavax.sql.XADataSourceinterfaces in the JDBC driver.-
any classname representing a JDBC driver (example:org.postgresql.Driver)
URL Database url of the form jdbc:<database_vendor_subprotocol>. This property may be used only for JDBC RA that implements the Driver (JDBC_DM) -
Any url valid for a database provider (example:jdbc:postgresql://localhost:5432/mydb)
user Database user name -
any name
password: Database password -
any string
loginTimeout Maximum time in seconds that the driver will wait while attempting to connect to a database. -
no value = 0 (default value)
-
n in seconds
isolationLevel Level of transaction isolation -
none
-
serializable
-
read_committed
-
read_uncommitted
-
repeatable_read
mapperName Name of the JORM mapper The possible values can be found in the List of available mappers in JORM documentation. databaseName Name of the database -
any name
description: Informal description -
any String
portNumber Port Number of the database server -
a number
serverName Name of the database server. -
any name
dbSpecificMethods allow flexibility to call setter methods on the dsClass as required by the database provider see below the particular syntax -
-
dbSpecificMethods a specific property:
The JOnAS JDBC Resource Adapter is built as a generic connector to any database provider. The limitation of this is that each database provider may have different requirements about the methods needed to configure the
dataSourceclass. This dbSpecificMethods property was added to allow flexibility to call setter methods on the dsClass as required by the database provider. The specific information about what additional methods should be used is documented by the database provider. The format of the value specified is:[:<del_char>]<method>=<value>::<value_type>:<method>=<value>::<value_type>....with:
: optional starting value that denotes using the next character as the delimiter instead of the default ':' <del_char> delimiter character to use <method> method to call followed by an = sign <value> the parameter value to pass to the method being called, followed by 2 delimiter characters.If a Properties object is being passed, then the format of this value must be (name=val, name=val, ...); <value_type> the parameter type used to construct the reflection call, followed by the delimiter character if additional methods are being called
-
Boolean or bool
-
Byte or byte
-
Character or char
-
Double or double
-
Float or float
-
Integer or int
-
Long or long
-
Properties or java.util.Properties
-
Short or short
-
String
-
At JDBC RA deployment time, if pool-init is not null pool-init JDBC connection are created.
When a user requests a jdbc connection, the JDBC RA first checks to see if a connection is already open for its transaction. If not, it tries to get a free connection from the free list. If there are no more connections available, it creates a new jdbc connection (if pool-max is not reached).
If it cannot create new connections, the user must wait (if
pool-max-waiters is not reached) until
a connection is released. After a limited time (pool-max-waittime), the getConnection
returns an exception.
When the user calls close() on its
connection, it is put back in the free list.
Many statistics are computed (every pool-sampling-period seconds) and can be viewed by JonasAdmin. This is useful for tuning these parameters and for seeing the server load at any time
When a connection has been open for a time too long (pool-max-age), the pool will try to release it from the freelist. However, the JDBC RA always tries to keep open at least the number of connections specified in pool-min.
When the user has forgotten to close a jdbc connection, the system can automatically close it, after pool-max-opentime minutes. Note that if the user tries to use this connection later, thinking it is still open, it will return an exception (socket closed).
When a connection is reused from the freelist, it is possible to verify that it is still valid. This is configured in jdbc-check-level . For levels >1 it tries a dummy statement on the connection before returning it to the caller. This statement is configured in jdbc-test-statement.
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
this previous description is not only true for JDBC RAs but also for all types of resource adapters, except jdbc-check-level and jdbc-test-statement which are specifics for JDBC. |
An RAR for Oracle named as jdbc_1 in JNDI and
using the Oracle thin Driver JDBC driver, should be described in a file
(called for example Oracle1_DM.rar), with the
following properties configured in the jonas-ra.xml file:
<?xml version = "1.0" encoding = "UTF-8"?>
<jonas-connector xmlns="http://www.objectweb.org/jonas/ns"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.objectweb.org/jonas/ns
http://www.objectweb.org/jonas/ns/jonas-connector_4_2.xsd" >
<jndi-name>jdbc_1</jndi-name>
<rarlink>JOnASJDBC_DM</rarlink>
<jonas-config-property>
<jonas-config-property-name>user</jonas-config-property-name>
<jonas-config-property-value>scott</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>password</jonas-config-property-name>
<jonas-config-property-value>tiger</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>loginTimeout</jonas-config-property-name>
<jonas-config-property-value></jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>URL</jonas-config-property-name>
<jonas-config-property-value>jdbc:oracle:thin:@malte:1521:ORA1</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>dsClass</jonas-config-property-name>
<jonas-config-property-value>oracle.jdbc.driver.OracleDriver</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>mapperName</jonas-config-property-name>
<jonas-config-property-value>rdb.oracle</jonas-config-property-value>
</jonas-config-property>
</jonas-connector>
In this example, "malte" is the hostname of the server running the database Oracle, 1521 is the SQL*Net V2 port number on this server, and ORA1 is the ORACLE_SID. This example makes use of the Oracle "Thin" JDBC driver. For an application server running on the same host as the Oracle DBMS, you can use the Oracle OCI JDBC driver.
To create a PostgreSQL RAR configured as jdbc_3 in JNDI, it should be described in a file (called for examplePostgreSQL3_DM.rar), with the following properties configured in the jonas-ra.xml file:
<?xml version = "1.0" encoding = "UTF-8"?>
<jonas-connector xmlns="http://www.objectweb.org/jonas/ns"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.objectweb.org/jonas/ns
http://www.objectweb.org/jonas/ns/jonas-connector_4_2.xsd" >
<jndi-name>jdbc_3</jndi-name>
<rarlink>JOnASJDBC_DM</rarlink>
<jonas-config-property>
<jonas-config-property-name>user</jonas-config-property-name>
<jonas-config-property-value>jonas</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>password</jonas-config-property-name>
<jonas-config-property-value>jonas</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>loginTimeout</jonas-config-property-name>
<jonas-config-property-value></jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>URL</jonas-config-property-name>
<jonas-config-property-value>jdbc:postgresql:/malte:5432/db_jonas</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>dsClass</jonas-config-property-name>
<jonas-config-property-value>org.postgresql.Driver</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>mapperName</jonas-config-property-name>
<jonas-config-property-value>rdb.postgres</jonas-config-property-value>
</jonas-config-property>
</jonas-connector>
An RAR for Oracle configured as jdbc_4 in JNDI and using the
Oracle XADataSource interface of the JDBC driver
thin in order to use a JDBC2-XA-compliant driver.It may be described in
a file (called for example Oracle1_XA.rar), with the following
properties configured in the jonas-ra.xml file:
<?xml version = "1.0" encoding = "UTF-8"?>
<jonas-connector xmlns="http://www.objectweb.org/jonas/ns"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.objectweb.org/jonas/ns
http://www.objectweb.org/jonas/ns/jonas-connector_4_2.xsd" >
<jndi-name>jdbc_4</jndi-name>
<rarlink>JOnASJDBC_XA</rarlink>
<jonas-config-property>
<jonas-config-property-name>user</jonas-config-property-name>
<jonas-config-property-value>jonas</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>password</jonas-config-property-name>
<jonas-config-property-value>jonas</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>databaseName</jonas-config-property-name>
<jonas-config-property-value>dbjonas</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>portNumber</jonas-config-property-name>
<jonas-config-property-value>1521</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>serverName</jonas-config-property-name>
<jonas-config-property-value>wallis</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>dbSpecificMethods</jonas-config-property-name>
<jonas-config-property-value>:#setDriverType=thin##String</jonas-config-property-value>
</jonas-config-property>
<jonas-config-property>
<jonas-config-property-name>dsClass</jonas-config-property-name>
<jonas-config-property-value>oracle.jdbc.xa.client.OracleXADataSource</jonas-config-property-value>
</jonas-config-property>
</jonas-connector>
The P6Spy tool is integrated into JOnAS and it provides an easy way to trace the SQL requests sent to the database.
To enable this tracing feature, perform the following configuration steps:
-
Update the appropriate RAR file's
jonas-ra.xmlfile by setting the dsClass property tocom.p6spy.engine.spy.P6SpyDriver -
Set the realdriver property in the
spy.propertiesfile (located in$JONAS_BASE/conf)to the jdbc driver of your actual database. -
Verify that logger.org.objectweb.jonas.jdbc.sql.level is set to DEBUG in $JONAS_BASE/conf/trace.properties.
Example jonas-ra.xml content:
<?xml version = "1.0" encoding = "UTF-8"?> <jonas-connector xmlns="http://www.objectweb.org/jonas/ns" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.objectweb.org/jonas/ns http://www.objectweb.org/jonas/ns/jonas-connector_4_2.xsd" > <jndi-name>jdbc_3</jndi-name> <rarlink>JOnASJDBC_DM</rarlink> <native-lib></native-lib> <log-enabled>true</log-enabled> <log-topic>org.objectweb.jonas.jdbc.DMPostgres</log-topic> <pool-params> <pool-init>0</pool-init> <pool-min>0</pool-min> <pool-max>100</pool-max> <pool-max-age>0</pool-max-age> <pstmt-max>10</pstmt-max> </pool-params> <jdbc-conn-params> <jdbc-check-level>0</jdbc-check-level> <jdbc-test-statement></jdbc-test-statement> </jdbc-conn-params> <jonas-config-property> <jonas-config-property-name>user</jonas-config-property-name> <jonas-config-property-value>jonas</jonas-config-property-value> </jonas-config-property> <jonas-config-property> <jonas-config-property-name>password</jonas-config-property-name> <jonas-config-property-value>jonas</jonas-config-property-value> </jonas-config-property> <jonas-config-property> <jonas-config-property-name>loginTimeout</jonas-config-property-name> <jonas-config-property-value></jonas-config-property-value> </jonas-config-property> <jonas-config-property> <jonas-config-property-name>URL</jonas-config-property-name> <jonas-config-property-value>jdbc:postgresql://your_host:port/your_db</jonas-config-property-value> </jonas-config-property> <jonas-config-property> <jonas-config-property-name>dsClass</jonas-config-property-name> <jonas-config-property-value>com.p6spy.engine.spy.P6SpyDriver</jonas-config-property-value> </jonas-config-property> <jonas-config-property> <jonas-config-property-name>mapperName</jonas-config-property-name> <jonas-config-property-value>rdb.postgres</jonas-config-property-value> </jonas-config-property> <jonas-config-property> <jonas-config-property-name>logTopic</jonas-config-property-name> <jonas-config-property-value>org.objectweb.jonas.jdbc.DMPostgres</jonas-config-property-value> </jonas-config-property> </jonas-connector>In
$JONAS_BASE/conf/spy.propertiesfile:realdriver=org.postgresql.Driver
In
$JONAS_BASE/conf/trace.properties:logger.org.objectweb.jonas.jdbc.sql.level DEBUG
The migration of a Database.properties file to
a similar Resource Adapter can be accomplished through the execution of
the following RAConfig tool command. Refer to the JOnAS Commands Reference Guide for
a complete description of RAConfig command.
RAConfig -dm -p MySQL1 $JONAS_ROOT/rars/autoload/JOnAS_jdbcDM MySQL_dm
Generates a MySQL_dm.rar file linked to
JOnAS_jdbcDM.rar, the jonas-ra.xml
file inserted is created with values coming from the
ra.xml file of the
JOnAS_jdbcDM.rar and values from the
MySQL1.properties file
The jonas-ra.xml created by the previous
command can be updated further, if desired. Once the additional properties
have been configured, update the MySQL_dm.rar file
using the following command:
RAConfig -path . MySQL_dm.rarRAConfig -u jonas-ra.xml MySQL_dm.rar
JMS Resource adapters can be deployed, either via the
jonas.properties file, or via the JonasAdmin tool, or
included in the autoload directory of the resource
service.
JMS connections are obtained from a JMS RA, which is configured to identify and access a JMS server.
The JORAM resource adapter archive
(joram_for_jonas_ra.rar) is provided with the JOnAS
distribution. It is located in the $JONAS_ROOT/rars/autoload directory and thus is
deployed automatically.
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
jms must not appear in the list of
services of the |
The JORAM RA may be seen as the central authority to go through for connecting and using a JORAM platform. The RA is provided with a default deployment configuration which:
-
Starts a collocated JORAM server in non-persistent mode, with id 0 and name s0, on host localhost and using port 16010; for doing so it relies on both an
a3server.xmlfile located in the$JONAS_BASE/confdirectory and the jonas-ra.xml file located within the RA. -
Creates managed JMS ConnectionFactory instances and binds them with the names CF, QCF, and TCF.
-
Creates administered objects for this server (JMS destinations and non-managed factories) as described by the
joramAdmin.xml, located in the$JONAS_BASE/confdirectory; those objects are bound with the names sampleQueue, sampleTopic, JCF, JQCF, and JTCF.
This default behaviour is strictly equivalent to the default jms service's behaviour.
The default configuration may, of course, be modified.
The JORAM integration into JOnAS is composed of 3 different parts: server, RA, and administration. Each part contains its own configuration files:
-
a3servers.xml is the JORAM platform configuration file, i.e. the server part. The file is located in the
$JONAS_BASE/confdirectory. -
ra.xmlandjonas-ra.xmlare the resource adapter configuration files. They are embedded in the resource adapter (META-INF directory). -
joramAdmin.xmlcontains the administration tasks to be performed by the JORAM server such as the JMS objects creation. It is located in the$JONAS_BASE/confdirectory.
The a3server.xml
($JONAS_BASE/conf/a3server.xml) file describes the
JORAM platform, i.e., the network domain, the used transport protocol,
and the reachable JORAM servers. It is used by a JORAM server at start
time. By default, only one collocated JORAM server is defined (s0) based
on the tcp/ip protocol. A distributed configuration example is provided
in the how-to document and other examples are available in JORAM's user
guide.
<config> <property name="Transaction" value="fr.dyade.aaa.util.NullTransaction"/><server id="0" name="S0" hostname="localhost">
<service class="org.objectweb.joram.mom.proxies.ConnectionManager" args="root root"/> <service class="org.objectweb.joram.mom.proxies.tcp.TcpProxyService" args="16010"/>
</server> </config>
|
This property means that the non persistent mode for JMS is choosen. In order to use persistent mode, the value must be changed to "fr.dyade.aaa.util.NTransaction" |
|
|
Here can be set the server id and the host where the server run |
|
|
args specifies the port number the JORAM server is listening on |
The above configuration describes a JORAM platform made up of one unique JORAM server (id 0, name s0), running on localhost, listening on port 16010. Those values are taken into account by the JORAM server when starting. However, they should match the values set in the deployment descriptor of the RA, otherwise the adapter either will not connect to the JORAM server, or it will build improper connection factories.
The joram_raconfig command allows to modify these parameters in all the configuration files.
If used in non-collocated mode, joram can be started with the JmsServer command which loads the $JONAS_BASE/conf/a3server.xml configuration file.
The ra.xml file is the standard deployment
descriptor for the JORAM adapter and the jonas-ra.xml
file is the JOnAS-specific deployment descriptor for the
JORAM adapter. These files set the central configuration of the adapter,
define and set managed connection factories for outbound communication,
and define a listener for inbound communication. jonas-ra.xml
contains specific parameters such as pool parameters or jndi
names, but also may redefine the parameters of some ra.xml
files and override their values. Globally, a good way to
proceed is to keep the original ra.xml file with
the default values and to customize the configuration only in the
jonas-ra.xml file.
Changing the configuration of the RA requires extracting and editing the deployment descriptor and updating the archive file. There are several possible ways to do this:
-
With the RAConfig command to extract jonas-ra.xml, do the following:
RAConfig -path . joram_for_jonas_ra.rar
Then, to update the archive, do the following:
RAConfig -u jonas-ra.xml joram_for_jonas_ra.rar
-
Through the jonasAdmin console (refer to Administration guide for a complete description).
In the jonasAdmin's tree, the Resource Adapter Module node (under the deployment node) contains a configure tab that allows editing of both the ra.xml file and the jonas-ra.xml file of the undeployed RA.
-
Through the joram_raconfig utility (refer to joram_raconfig description for a complete description).
This tool allows easy modification to the network parameters of the JORAM server in all the configuration files.
The following properties are related to the central configuration of the adapter; they are set via some <jonas-config-property> elements:
| property name | description | possible values |
| CollocatedServer | Running mode of the JORAM server to which the adapter gives access. |
|
| PlatformConfigDir | Directory where the a3servers.xml
and joramAdmin.xml files are
located. |
|
| PersistentPlatform | Persistence mode of the collocated JORAM server. - not taken into account if the JORAM server is set as non-collocated. - If true, set the property 'Transaction' to 'fr.dyade.aaa.util.NTransaction' before launching the JORAM server. - If false, set the property 'Transaction' to 'fr.dyade.aaa.util.NullTransaction' before launching the JORAM server. - Warning, if the 'Transaction' property is set in the a3server.xml file, this value is ignored. |
|
| ServerId | Identifier of the JORAM server to start (not taken into account if the JORAM server is set as non-collocated). |
|
| ServerName | Logical name of the JORAM server to start.In the collocated case, this parameter specifies the storage path of the persistent mode (absolute or relative path). If the JORAM server is non-collocated, it must be set to the name of the already started JORAM server (this is necessary for management purpose). |
|
| AdminFileXML | Name of the file describing the administration tasks to be performed by the JORAM server, i.e., JMS destinations to create, users to create, ... If the file does not exist, or is not found, no administration task is performed. |
|
| HostName | Name of the host where the JORAM server runs, used for accessing a remote JORAM server (non-collocated mode), and for building appropriate connection factories. |
|
| ServerPort | Port the JORAM server is listening on, used for accessing a remote JORAM server (non-collocated mode), and for building appropriate connection factories. |
|
| ConnectingTimer | Duration in seconds during which connecting is attempted (connecting might take time if the server is temporarily not reachable) |
|
| CnxPendingTimer | Period in milliseconds between two ping requests sent by the client connection to the server; |
|
| TxPendingTimer | Duration in seconds during which a JMS transacted (non XA) session might be pending; above that duration the session is rolled back and closed. |
|
| DeleteDurableSubscription | Indicates the durable Subscriptions must be deleted when the consumer is closed |
|
The <jonas-connection-definition> elements wrap properties related to the managed connection factories:
There are three managed connection factories:
-
A Queue managed connection factory registered in JNDI with the name QCF
-
A Topic managed connection factory registered in JNDI with the name TCF
-
A managed connection factory registered in JNDI with the name CF
Here are the properties that can be configured for each managed connection factory:
| property name | description | possible values |
| jndi-name | Name used for binding the constructed connection factory. |
Any name (ex: myQueueConnectionFactory). Default values are
|
| UserName | Default user name that will be used for opening JMS connections. |
|
| Password | Default user password that will be used for opening JMS connections. |
|
| Collocated | Specifies if the connections that will be created from the factory should be TCP or local-optimized connections |
|
The <jonas-activationspec> element wraps a property related to inbound messaging:
| property name | description | possible values |
| jndi-name | Binding name of a JORAM object to be used by 2.1 MDBs. |
|
The Pooling Tags are the same than those for other RAs:
| property name | description | possible values |
| pool-init | Initial size of the managed connection pool |
|
| pool-min | Minimum size of the managed connection pool. |
|
| pool-max | Maximum size of the managed connection pool. |
|
| pool-max-age-minutes | Maximum number of minutes to keep the managed connection in the pool. |
|
| pstmt-max | Maximum number of PreparedStatements per managed connection in the pool. Only needed with the JDBC RA of JOnAS or another database vendor's RAR. Value of 0 is unlimited and -1 disables the cache. |
|
| pool-max-opentime | Identifies the maximum number of minutes that a managed connection can be left busy. |
|
| pool-max-waiters: | identifies the maximum number of waiters for a managed connection. Default value is 0. |
|
| pool-max-waittime | identifies the maximum number of seconds that a waiter will wait for a managed connection. Default value is 0. |
|
| pool-sampling-period: | identifies the number of seconds that will occur between statistics samplings of the pool. Default is 30 seconds. |
|
joramAdmin.xml file describes the
configuration related to the application. It describes the
administration objects in the JORAM server such as the JMS objects, the
users, or the non-managed factories. In other words, it defines the
JORAM objects to be (optionally) created when deploying the
adapter.
In earlier version the joram-admin.cfg was
used for this same purpose but it is now deprecated.
The default file provided with JOnAS creates a queue bound with the name sampleQueue, a topic bound with the name sampleTopic, sets the anonymous user, and creates and binds non-managed connection factories named JCF, JQCF and JTCF
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
The format of this file is XML. Here are some examples:
-
simple example:
<?xml version="1.0"?> <JoramAdmin> <AdminModule> <collocatedConnect name="root" password="root"/> </AdminModule> <ConnectionFactory className="org.objectweb.joram.client.jms.tcp.TcpConnectionFactory"> <tcp host="localhost" port="16010"/> <jndi name="JCF"/> </ConnectionFactory> <ConnectionFactory className="org.objectweb.joram.client.jms.tcp.QueueTcpConnectionFactory"> <tcp host="localhost" port="16010"/> <jndi name="JQCF"/> </ConnectionFactory> <ConnectionFactory className="org.objectweb.joram.client.jms.tcp.TopicTcpConnectionFactory"> <tcp host="localhost" port="16010"/> <jndi name="JTCF"/> </ConnectionFactory> <User name="anonymous" password="anonymous" serverId="0"/> <Queue name="sampleQueue"> <freeReader/> <freeWriter/> <jndi name="sampleQueue"/> </Queue> <Topic name="sampleTopic"> <freeReader/> <freeWriter/> <jndi name="sampleTopic"/> </Topic> </JoramAdmin> -
For requesting the creation of a new object, simply add the element in the file. For example, to add a queue 'MyQueue', add the following XML element:
<Queue name="myQueue"> <freeReader/> <freeWriter/> <jndi name="myQueue"/> </Queue> -
When the JORAM is not collocated, the AdminModule must be defined as follows:
<AdminModule> <connect host="localhost" port="16020" name="root" password="root"/> </AdminModule>The port number must be set with the server port number (defined in the
a3servers.xmland in the JORAM's RAR configurationra.xmlandjonas-ra.xmlfiles). -
Possible parameters for a queue definition:
<Queue name="" serverId="" className="" dmq="" nbMaxMsg="" threshold=""> <property name="" value=""/> <property name="" value=""/> <reader user=""/> <writer user=""/> <freeReader/> <freeWriter/> <jndi name=""/> </Queue> -
Possible parameters for a topic definition:
<Topic name="" parent="" serverId="" className="" dmq=""> <property name="" value=""/> <property name="" value=""/> <reader user=""/> <writer user=""/> <freeReader/> <freeWriter/> <jndi name=""/> </Topic> -
Example of a dead message queue definition:
<DMQueue name="DMQ" serverId="0"> <reader user="anonymous"/> <writer user="anonymous"/> <freeReader/> <freeWriter/> <jndi name="DMQ"/> </DMQueue> -
Example of a scheduler queue definition:
<Destination type="queue" serverId="0" name="schedulerQueue" className="com.scalagent.joram.mom.dest.scheduler.SchedulerQueue"> <freeReader/> <freeWriter/> <jndi name="schedulerQueue"/> </Destination> -
Example of a clustered queues destination:
<Cluster> <Queue name="queue0" serverId="0" className="org.objectweb.joram.mom.dest.ClusterQueue"> <freeReader/> <freeWriter/> <property name="period" value="10000"/> <property name="producThreshold" value="50"/> <property name="consumThreshold" value="2"/> <property name="autoEvalThreshold" value="false"/> <property name="waitAfterClusterReq" value="1000"/> <jndi name="queue0"/> </Queue> <Queue name="queue1" serverId="1" className="org.objectweb.joram.mom.dest.ClusterQueue"> <freeReader/> <freeWriter/> <property name="period" value="10000"/> <property name="producThreshold" value="50"/> <property name="consumThreshold" value="2"/> <property name="autoEvalThreshold" value="false"/> <property name="waitAfterClusterReq" value="1000"/> <jndi name="queue1"/> </Queue> <Queue name="queue2" serverId="2" className="org.objectweb.joram.mom.dest.ClusterQueue"> <freeReader/> <freeWriter/> <property name="period" value="10000"/> <property name="producThreshold" value="50"/> <property name="consumThreshold" value="2"/> <property name="autoEvalThreshold" value="false"/> <property name="waitAfterClusterReq" value="1000"/> <jndi name="queue2"/> </Queue> <freeReader/> <freeWriter/> <reader user="user0"/> <writer user="user0"/> <reader user="user1"/> <writer user="user1"/> <reader user="user2"/> <writer user="user2"/> </Cluster>
Change the parameters (host, port, server id) in the JORAM configuration files.
joram_raconfig
[-p port]
[-h host]
[-s serverId]
- -p port
-
Set the listening port of the JORAM server
- -h host
-
Set the IP address of the JORAM server
- -s serverId
-
Set the server id of the JORAM server
The joram_raconfig tool aims to facilitate changes for the parameters (host, port, server id) in the JORAM configuration files.
JORAM relies on several configuration files:
a3servers.xml, joramAdmin.xml,
ra.xml. With joram_raconfig, all these
configuration files are updated and thus the consistency is
ensured.
Files modified:
-
$JONAS_BASE/conf/a3servers.xml -
$JONAS_BASE/conf/joramAdmin.xml -
$JONAS_BASE/deploy/joram_ra_for_jonas_ra.rarin which the fileMETA_INF/ra.xmlis updated.
A pool of ManagedConnection is defined for each factory (connection definition) specified in the jonas-ra.xml file. See the pool parameters in the Section 2.7.1.2, “Resource Adapter configuration: ra.xml, jonas-ra.xml”.
The JORAM RA manages a pool of session/thread for each connection and, by default, the maximum number of parallel sessions is set to 10.
When linked with an message-driven bean, this maximum number of entries in the pool corresponds to the maximum number of messages that can be processed in parallel per message-driven bean. A session is released to the pool just after the message processing (onMessage()). When the maximum is reached, the inquiries for a session creation are blocked until a session becomes available in the pool.
The maxNumberOfWorks property can be set in the message-driven bean standard deployment descriptor. For example, the code below can be added to limit the number of parallel sessions to 100 (default value is 10).
<activation-config-property>
<activation-config-property-name>maxNumberOfWorks</activation-config-property-name>
<activation-config-property-value>100</activation-config-property-value>
</activation-config-property>
As this parameter set the max number of messages that can be treated simultaneously, the max-cache-size must be set accordingly in the specific deployment descriptor.
Undeploying a JORAM adapter either stops the collocated JORAM server or disconnects from a remote JORAM server. It is then possible to deploy the same adapter again. If set for running a collocated server, it will re-start it. If the running mode is persistent, then the server will be retrieved in its pre-undeployment state (with the existing destinations, users, and possibly messages). If set for connecting to a remote server, the adapter will reconnect and access the destinations it previously created.
In the collocated persistent case, if the intent is to start a brand new JORAM server, its persistence directory should be removed. This directory is located in JOnAS' running directory and has the same name as the JORAM server (for example, s0/ for server "s0").
This section describes how to configure the Datasources for connecting application to databases when the dbm service is used.
For both container-managed or bean-managed persistence, JOnAS makes use of relational
storage systems through the JDBC interface. JDBC connections are obtained
from an object, the DataSource, provided at the
application server level. The DataSource interface
is defined in the JDBC standard extensions.
A DataSource object identifies a database and
a means to access it via JDBC (a JDBC driver). An application server may
request access to several databases and thus provide the corresponding
DataSource objects that will be registered in JNDI
registry.
This section explains how DataSource objects
can be defined and configured in the JOnAS server.
JOnAS
provides a generic driver-wrapper that emulates the
XADataSource interface on a regular JDBC driver. It
is important to note that this driver-wrapper does not ensure a real
two-phase commit for distributed database transactions.
Neither the EJB specification nor the Java EE specification describe how
to define DataSource objects so that they are
available to a Java EE
platform. Therefore, this document, which describes how to define and
configure DataSource objects, is specific to JOnAS. However, the way to
use these DataSource objects in the Application
Component methods is standard, that is, by using the resource manager
connection factory references (refer to the example in the section Writing database access
operations of the Developing Entity Bean
Guide).
A DataSource object should be defined in a
file called <DataSource name>.properties (for example
Oracle1.properties for an Oracle DataSource or Postgres.properties for an
PostgreSQL DataSource.These files must be located in $JONAS_BASE/conf directory.
In the jonas.properties file, to define a
DataSource "Oracle1.properties" add the name "Oracle1" to the line
onas.service.dbm.datasources, as follows:
jonas.service.dbm.datasources Oracle1, Sybase, PostgreSQL
The property file defining a DataSource may
contain two types of information:
-
connection properties
-
JDBC Connection Pool properties
| property name | Description |
| datasource.name | JNDI name of the DataSource |
| datasource.url | The JDBC database URL : jdbc:<database_vendor_subprotocol>:... |
| datasource.classname | Name of the class implementing the JDBC driver |
| datasource.username | Database user name |
| datasource.password | Database user password |
| datasource.isolationLevel |
Database isolation level for transactions. Possible values are:
The default depends on the database used. |
| datasource.mapper | JORM database mapper (for possible values see here) |
Each Datasource is implemented as a
connection manager and manages a pool of JDBC connections.
The pool can be configured via some additional properties described in the following table.
All these settings have default values and are not required. All these attributes can be reconfigured when JOnAS is running, with the console JonasAdmin.
| property | Description | Default value |
| jdbc.connchecklevel |
JDBC connection checking level:
|
1 |
| jdbc.connteststmt | test statement in case jdbc.connchecklevel = 2. | select 1 |
| jdbc.connmaxage | nb of minutes a connection can be kept in the pool. After this time, the connection will be closed, if minconpool limit has not been reached. | 1440 mn (= 1 day) |
| jdbc.maxopentime | Maximum time (in mn) a connection can be left busy. If the caller has not issued a close() during this time, the connection will be closed automatically. | 1440 mn (= 1 day) |
| jdbc.minconpool | Minimum number of connections in the pool. Setting a positive value here ensures that the pool size will not go below this limit during the datasource lifetime. | 0 |
| jdbc.maxconpool | Maximum number of connections in the pool. Limiting the max pool size avoids errors from the database. | no limit |
| jdbc.samplingperiod | Sampling period for JDBC monitoring. nb of seconds between 2 measures. | 60 sec |
| jdbc.maxwaittime | Maximum time (in seconds) to wait for a connection in case of shortage. This is valid only if maxconpool has been set. | 10 sec |
| jdbc.maxwaiters | Maximum of concurrent waiters for a JDBC Connection. This is valid only if maxconpool has been set. | 1000 |
| jdbc.pstmtmax | Maximum number of prepared statements cached in a Connection. Setting this to a bigger value (120 for example) will lead to better performance, but will use more memory. The recommendation is to set this value to the number of different queries that are used the most often. This is to be tuned by administrators. | 12 |
When a user requests a jdbc connection, the dbm connection manager first checks to see if a connection is already open for its transaction. If not, it tries to get a free connection from the free list. If there are no more connections available, the dbm connection manager creates a new jdbc connection (if jdbc.maxconpool is not reached).
If it cannot create new connections, the user must wait (if
jdbc.maxwaiters is not reached) until a connection
is released. After a limited time
(jdbc.maxwaittime), the getConnection
returns an exception.
When the user calls close() on its
connection, it is put back in the free list.
Many statistics are computed (every jdbc.samplingperiod seconds) and can be viewed by JonasAdmin. This is useful for tuning these parameters and for seeing the server load at any time.
When a connection has been open for too long a time (jdbc.connmaxage), the pool will try to release it from the freelist. However, the dbm connection manager always tries to keep open at least the number of connections specified in jdbc.minconpool.
When the user has forgotten to close a jdbc connection, the system can automatically close it, after jdbc.maxopentime minutes. Note that if the user tries to use this connection later, thinking it is still open, it will return an exception (socket closed).
When a connection is reused from the freelist, it is possible to verify that it is still valid. This is configured in jdbc.connchecklevel. The maximum level is to try a dummy statement on the connection before returning it to the caller. This statement is configured in jdbc.connteststmt
Here is the template for an Oracle dataSource.properties file that can be found in $JONAS_ROOT/conf:
###################### Oracle DataSource configuration example
#
#####
# DataSource configuration
#
datasource.name jdbc_1
datasource.url jdbc:oracle:thin:@<your-hostname>:1521:<your-db>
datasource.classname oracle.jdbc.driver.OracleDriver
datasource.username <your-username>
datasource.password <user-password>
datasource.mapper rdb.oracle
#####
# ConnectionManager configuration
#
# JDBC connection checking level.
# 0 = no special checking
# 1 = check physical connection is still open before reusing it
# 2 = try every connection before reusing it
jdbc.connchecklevel 0
# Max age for jdbc connections
# nb of minutes a connection can be kept in the pool
jdbc.connmaxage 1440
# Maximum time (in mn) a connection can be left busy.
# If the caller has not issued a close() during this time, the connection
# will be closed automatically.
jdbc.maxopentime 60
# Test statement
jdbc.connteststmt select * from dual
# JDBC Connection Pool size.
# Limiting the max pool size avoids errors from database.
jdbc.minconpool 10
jdbc.maxconpool 30
# Sampling period for JDBC monitoring :
# nb of seconds between 2 measures.
jdbc.samplingperiod 30
# Maximum time (in seconds) to wait for a connection in case of shortage.
# This may occur only when maxconpool is reached.
jdbc.maxwaittime 5
# Maximum of concurrent waiters for a JDBC Connection
# This may occur only when maxconpool is reached.
jdbc.maxwaiters 100
The P6Spy tool is integrated within JOnAS to provide a means for easily tracing the SQL requests that are sent to the database.
To enable this tracing feature, perform the following configuration steps:
-
set the datasource.classname property of your datasource properties file to
com.p6spy.engine.spy.P6SpyDriver -
set the realdriver property in the
spy.propertiesfile (located within$JONAS_BASE/conf)to the jdbc driver of your actual database -
verify that logger.org.objectweb.jonas.jdbc.sql.level is set to DEBUG in
$JONAS_BASE/conf/trace.properties.
Example of dataSource properties file:
datasource.name jdbc_3
datasource.url jdbc:postgresql://your_host:port/your_db
datasource.classname com.p6spy.engine.spy.P6SpyDriver
datasource.username jonas
datasource.password jonas
datasource.mapper rdb.postgres
Within JONAS_BASE/conf/spy.properties file:
realdriver=org.postgresql.Driver
Within JONAS_BASE/conf/trace.properties:
logger.org.objectweb.jonas.jdbc.sql.level DEBUG
[1] for each category the alphabetical of the file names is taken
[2] see Understanding class loader hierarchy for a complete description of the classloader mechanism.
[3] jonathan.xml is used for configuring the jeremie protocol which is deprecated
[4] the name can be changed via
jonas.log.configfile property in
jonas.properties
[5] By default automatic is set for the handler logf
[6] this property is optional and its default value is 'yes'
[7] There is no real acronym for this specification JCA was the acronym for Java Cryptography Architecture . In the rest of this document we will use J2CA
[8] JOnAS has been tested with Apache jUDDI, an ASL2 UDDI v2 implementation.
[9] all these handlers are defined in the package
org.objectweb.jonas.security.auth.callback
As with other Apache modules, mod_jk should be first
installed on the modules directory of the Apache Web
Server and the
httpd.conf
file has to be updated. Moreover, mod_jk requires
workers.properties
file that describes the host(s) and port(s) used by the
workers.
Here we provide a
workers.properties
file to connect the frontal with two
JkCluster
members. The file defines a
load-balancing
worker named
myloadbalancer
, and the two
balanced
workers,
worker1
and
worker2
. Each cluster member will be configured to play the
role of one of the balanced workers. Additionally, a
status worker jkstatus is defined for managing load
balancers.
#-----------------------
# List the workers name
#-----------------------
worker.list=myloadbalancer,jkstatus
#-----------------------
# worker1
#-----------------------
worker.worker1.port=9010
worker.worker1.host=localhost
worker.worker1.type=ajp13 # Load balance factor
worker.worker1.lbfactor=1 # Define preferred
failover node for worker1
#worker.worker1.redirect=worker2 # Disable worker1 for all requests except failover
#worker.worker1.disabled=True
#-----------------------
# worker2
#-----------------------
worker.worker2.port=9011
worker.worker2.host=localhost
worker.worker2.type=ajp13 # Load balance factor
worker.worker2.lbfactor=1 # Define preferred failover node for worker2
#worker.worker2.redirect=worker2 # Disable worker2 for all requests except failover
#worker.worker2.disabled=True
#-----------------------
# Load Balancer worker
#-----------------------
worker.myloadbalancer.type=lb
worker.myloadbalancer.balanced_workers=worker1,worker2
worker.mylloadbalancer.sticky_session=false
#-----------------------
# jkstatus worker
#-----------------------
worker.jkstatus.type=status
For a complete documentation about
workers.properties
see the Apache Tomcat Connector
guide
.
Here is information which should be customized and
set in
httpd.conf
directly or included from another file:
# Load mod_jk module
# Update this path to match your modules location
LoadModule jk_module
modules/mod_jk.so # Location of the workers.properties file
# Update this path to match your conf directory location (put workers.properties next to httpd.conf) JkWorkersFile
/etc/httpd/conf/workers.properties # Location of the log file JkLogFile /var/log/mod_jk.log
# Log level : debug, info, error or emerg
JkLogLevel info
# Select the timestamp log format
JkLogStampFormat "[%a %b %d %H:%M:%S %Y] "
# Shared Memory Filename ( Only for Unix platform ) required by loadbalancer
JkShmFile /var/log/jk.shm
# Assign specific URL to the workers
JkMount /clusteredExample myloadbalancer
JkMount /clusteredExample/* myloadbalancer
# A mount point to the status worker
JkMount /jkmanager jkstatus
JkMount /jkmanager/* jkstatus
# Enable the Jk manager access only from localhost
<Location /jkmanager/>
JkMount jkstatus
Order deny,allow
Deny from all
Allow from 127.0.0.1
</Location>
For a complete documentation see Apache HowTo .
Each member needs an AJP13 connector listening on the
port defined in the workers.properties file. Moreover,
the worker name (here worker1/worker2) must be used as
value for the Engine's
jvmRoute
attribute.
Here is a chunk of server.xml configurations file for the member worker1:
<Server>
<!-- Define the Tomcat Stand-Alone Service -->
<Service name="Tomcat-JOnAS">
<!-- Define a non-SSL Coyote HTTP/1.1 Connector on port 9000 -->
<Connector port="9000" maxHttpHeaderSize="8192" maxThreads="150"
minSpareThreads="25" maxSpareThreads="75"
enableLookups="false" redirectPort="9043"
acceptCount="100" connectionTimeout="20000"
disableUploadTimeout="true"/>
<!-- AJP 1.3 Connector on port 9010 for worker.worker1.port in workers.properties file -->
<Connector port="9010" enableLookups="false" redirectPort="9043" protocol="AJP/1.3"/>
<!-- An Engine represents the entry point You should set jvmRoute to support load-balancing via AJP ie : -->
<Engine name="jonas" defaultHost="localhost" jvmRoute="worker1">
</Engine>
</Service>
<Server>
The load-balancing is configured as a WEB farm.
Additionally to HTTP requests load balancing provided by TomcatCluster members, transparent failover for Web applications can be reached by using HTTP session replication provided by the Tomcat clustering solution.
TomcatCluster members are JOnAS instances having the web service activated, using the Tomcat implementation, and having a specific configuration which allows them to be members of a Tomcat cluster.
The concerned configuration file is the
server.xml
file. Every member of the cluster must have a Cluster
element defined in the default virtual host definition.
The cluster name is defined by the clusterName
attribute, which should be the same for all the cluster
members. Another common element for the cluster members
is the Membership definition.
The example below defines the configuration for a server which is a TomcatCluster member and a JkCluster member in the same time.
<Server>
<!-- Define the Tomcat Stand-Alone Service -->
<Service name="Tomcat-JOnAS">
<!-- Define a non-SSL Coyote HTTP/1.1 Connector on port 9000 -->
<Connector port="9000" maxHttpHeaderSize="8192" maxThreads="150"
minSpareThreads="25" maxSpareThreads="75"
enableLookups="false" redirectPort="9043"
acceptCount="100" connectionTimeout="20000"
disableUploadTimeout="true"/>
<!-- AJP 1.3 Connector on port 9010 (value of worker.worker1.port in workers.properties file) -->
<Connector port="9010" enableLookups="false" redirectPort="9043" protocol="AJP/1.3"/>
<!-- Define the Engine -->
<Engine name="jonas" defaultHost="localhost" jvmRoute="worker1">
</Engine>
<!-- Define the default virtual host -->
<Host name="localhost" debug="0" appBase="webapps"
unpackWARs="false" autoDeploy="false"
deployOnStartup="false" deployXML="false">
<!-- Define a Cluster element -->
<Cluster className="org.apache.catalina.cluster.tcp.SimpleTcpCluster"
clusterName="myTomcatCluster"
managerClassName="org.apache.catalina.cluster.session.DeltaManager"
expireSessionsOnShutdown="false" useDirtyFlag="true"
notifyListenersOnReplication="true">
<Membership
className="org.apache.catalina.cluster.mcast.McastService"
mcastAddr="228.0.0.4" mcastPort="45564"
mcastFrequency="500" mcastDropTime="3000"/>
<Receiver
className="org.apache.catalina.cluster.tcp.ReplicationListener"
tcpListenAddress="auto" tcpListenPort="4003"
tcpSelectorTimeout="100" tcpThreadCount="6"/>
<Sender
className="org.apache.catalina.cluster.tcp.ReplicationTransmitter"
replicationMode="pooled" ackTimeout="15000"/>
<Valve
className="org.apache.catalina.cluster.tcp.ReplicationValve"
filter=".*\.gif;.*\.js;.*\.jpg;.*\.png;.*\.htm;.*\.html;.*\.css;.*\.txt;"/>
</Cluster>
</Host>
</Service>
<Server>
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
the
clusterName
attribute is mandatory (and not set by default
in
|
Lets consider the two JOnAS servers which play the role
of
worker1
and
worker2
in the
myloadbalancer
JkCluster
. Suppose that these servers, named
node1
and
node2
are configured as members of the
myTomcatCluster
TomcatCluster
. The master detects automatically the Tomcat cluster
membership and creates a
TomcatCluster
named
myTomcatCluster
. It adds
node1
and
node2
to the cluster's member list.
Here is myTomcatCluster cluster with node1 and node2 members running
 |
CMI provides the following clustering features:
JNDI high availability through the registry replication and the multi-target lookup
-
EJB load-balancing and fail-over through the CMI cluster proxy
for the EJB2.1 home interface (SSB, SFSB, EB)
for the EJB2.1 remote interface (SSB)
for the EJB3 (SSB)
-
EJB high availability with the HA service
for the EJB2.1 SFSB

CMI can be enabled in JOnAS by:
setting the cmi protocol in the $JONAS_BASE/conf/carol.properties file
compiling an application with the CMI protocol
CMI brings its own registry for implementing the jndi replication. Each CMI registry instance over the cluster contains two areas:
a local area for hosting the local objects that must not be replicated
a distributed area hosting the global objects (cluster objects) that must be replicated
When an object is registered in the registry, the routing to the local or global area is done according to:
the type of the object: only the remote objects are replicated
the presence of the 'CMI class' having the same name as the object class with the suffix '_CMI' and inherited from the org.objectweb.carol.cmi.Distributor class
-
one of the two following methods returning true:
equivAtBind() if the replication has to take place at the bind() time. For example, this could be the case for the EJB Remote Home objects.
equivAtExport() if the replication has to take place at the export() time. Typically, this could be the case for the SSB Remote objects.
The entries of the distributed area are lists providing the ability, for example, to gather several stubs for the the same jndi-name and thus to return a stubs list.
CMI relies on JGroups group-communication protocol for ensuring the global registry replication. The parameters are gathered in the:
$JONAS_BASE/conf/carol.properties for specifying the JGroups configuration file name and the JGroups group name.
$JONAS_BASE/conf/jgroups-cmi.xml file for the settings of the jgroups protocol stack. By default, the JGroups configuration uses the UDP protocol and the multicast IP for broadcasting the registry updates. A TCP-based stack can be used in a network environment that does not allow the use of multicast IP or when a cluster is distributed over a WAN.

All the members of a cluster share the same JGroups configuration.
If several cluster partitions are required over a single LAN, several JGroups configurations must be configured with different values for the following parameters:
JGroups group name
JGroups multicast address
JGroups multicast port
When a new node appears in the cluster, its registry content is synchronized automatically.
When a node disappears, JGroups notifies the other's member of the node leaving and the registry entries related to this node are removed.
On the client side, the high availability of the registry is provided by the capability to set several JOnAS instances in the registry url. At the lookup time, the client chooses (round-robin algorithm) one of the available servers to get the home stub. If the server fails, the request is sent to another server. The CMI url registry is specified in the $JONAS_BASE/conf/carol.properties file using the following syntax:
carol.cmi.url=cmi://server1:port1[,server2:port2...]
Load-balancing and fail-over on the client side are provided through cluster-aware stubs. These stubs are generated on the fly through ASM and rely on:
the RMI/JRMP protocol for communicating with the server side,
the CMI class associated with the EJB for the load-balancing and fail-over logic.

The CMI cluster stub handles a cluster map on the client side. The CMI cluster stub is created:
at lookup time for the SSB, SFSB, EB Home objects if the retrieved object is replicated and located in the global registry
at create time for the SSB Remote objects if the retrieved object is replicated and located in the global registry
In these two cases, the call gets a stubs list from the global registry and the CMI cluster stub updates the local cluster map. Afterwards, the local cluster map can be updated dynamically during the invocation of the business methods calls (through the HA interceptors) when a new view is detected in the cluster.
If a communication error with a server occurs during a remote call invocation, the server is removed from the cluster map.
CMI classes are generated by GenIC when compiling with the protocol CMI. They are built from the velocity templates located in $JONAS_ROOT/templates/genic directory. By default the templates used are:
ClusterHomeDistributor.vm for the home interface of the SSB, SFSB, EB
ClusterRemoteSLSBDistributor.vm for the remote interface of the SSB
The templates inherit the org.objectweb.carol.cmi.Distributor class and contain the following methods:
-
choose(method, params) : this method is called by the CMI cluster stub at each remote method call to choose the next stub to use for invoking the call. By default, this method implements the weighted round-robin algorithm with a local preference, i.e., if there is a collocated server, it will be selected in priority. The servers factors are set for each JOnAS instance in the $JONAS_BASE/conf/carol.properties file.Below is given the code of the choose() method implementing a simple RR algorithm :
public StubData choose(Method method, Object[] parameters) throws NoServerException { Set stubs = getCurrentState(); if (lastSet != stubs) { lastSet = stubs; rr.update(stubs); } return rr.get(); } -
onException(method, params, stub, exception) : this method is called by the CMI cluster stub when an exception occurs and returns a decision of RETRY, RETURN, or THROW for indicating the behavior to the CMI smart stub. By default, this method returns a RETRY decision if the exception is related to a network error, and otherwise it returns a THROW decision. Below is given the code of the mustFailover() method that is used by default for analysing the exception and deciding if the fail-over must occur :
protected static boolean mustFailover(Exception ex) { if (ex instanceof UnmarshalException) { Throwable cause = ((UnmarshalException) ex).getCause(); if (( cause instanceof EOFException) || (cause instanceof SocketException)) { return true; } } if ((ex instanceof ConnectException) || (ex instanceof ConnectIOException) || (ex instanceof NoSuchObjectException)) { return true; } return false; } onReturn(method, params, stub, returnValue) : this method is called by the CMI cluster stub after having invoked the call and before returning to the application. This call back enables implementation of a post-processing on the return value. By default, this method does nothing.
The user has the ability to customize the load-balancing and fail-over logic for each EJB by specifying the velocity template to use in the JOnAS- specific descriptor on deployment of the ejb-jar file. The XML elements are:
<cluster-home-distributor>MyHomeDistributor.vm</cluster-home-distributor>
<cluster-remote-distributor>MyRemoteDistributor.vm</cluster-remote-distributor>
If not set, the default velocity templates are used.
If set with the value 'disabled', the CMI classes are not generated and the EJB will not be distributed.
If set with a file name, this file must be located in the $JONAS_ROOT/templates/genic directory.
The 'cluster-home-distributor' element is valid for the SSB, SFSB and EB.
The 'cluster-remote-distributor' element is valid for the SSB.
Stateful session beans (SFSBs) can be replicated since JOnAS 4.7 in order to provide high availability in the case of failures in clustered environments. A new service called High Availability (HA) has been included in JOnAS to provide replication mechanishms. JOnAS HA also requires the cluster method invocation (CMI) protocol.
Compared to JOnAS 4.7, JOnAS 4.8 implements a new replication algorithm based on a horizontal replication approach. The algorithm improves the algorithm implemented for JOnAS 4.7 with the following enhancements:
Replication of SFSBs with references to EBs: The algorithm can replicate SFSBs that reference EB by means of both, local or remote interfaces.
Transaction awareness: The algorithm is transaction aware, meaning that the state is not replicated if the transaction aborts.
Exactly-once semantics: Each transaction is committed exactly once at the DB if the client does not fail. If the client fails, each transaction is committed at most once at the DB
JOnAS implements an update-everywhere replication protocol according to the database replication terminology (See the J. Gray et al.'s paper ''The dangers of replication and a solution'' in proceedings of the ACM SIGMOD 96's conference, Canada). In this protocol, a client can connect to any server. When the client calls the create() method on the SFSB's Home interface, the server the client connects to is selected following a round-robin scheme. All the requests from the client to the SFSB will be processed by this server until the client calls the remove() method on the remote interface. The rest of the servers will act as backups for that client. Before sending the response to the client, the SFSB's state is sent to the backups.
If the server fails, another server among the backups will be selected to serve the client requests, first restoring the current state of the SFSBs from the state information stored in the HA local service. From this point on, this server will receive the new client requests.
The supported replication scenarios are shown in the following figure:

The horizontal approach aims to guarantee that the transactions are kept consistent when a fail-over occurs. They are either aborted or restored for ensuring the exactly-once semantics. During a fail-over, the new primary uses a special table in the database for storing the transaction identifier and enabling to find out if the transaction was committed or not.
If the transaction is aborted due to the primary failure, then the new primary will not find the transaction identifier in the special table. The request will be replayed.
If the transaction is committed, then the new primary will find the transaction identifier, which means that the transaction was committed. The request won't be replayed; the replicated result is returned.
Beyond the SFSB replication, the algorithm enables the building of applications (stateful or stateless) with a high level of reliability and integrity.
The High Availability (HA) service is required in JOnAS in order to replicate SFSBs. The HA service must be included in the list of available services in JOnAS. This is done in the jonas.properties file placed in $JONAS_BASE/conf.
... jonas.services registry,jmx,jtm,db,dbm,security,resource,ejb,ws,web,ear,ha ...
The HA service must also be configured in the jonas.properties file:
...
jonas.service.ha.class org.objectweb.jonas.ha.HaServiceImpl
jonas.service.ha.gcl jgroups
...
The HA service uses JGroups as a group communication layer (GCL). JGroups behavior is specified by means of a stack of properties configured through an XML file (See JGroups documentation for more information: http://www.jgroups.org). The default configuration of the HA service uses the $JONAS_BASE/conf/jgroups-ha.xml file and the sfsb-rep group name. The HA service can be told to use a particular stack configuration or a particular group name by modifying the following lines in jonas.properties:
... jonas.service.ha.jgroups.conf jgroups-ha.xml jonas.service.ha.jgroups.groupname jonas-rep ...
Finally, the CMI protocol must be specified in the carol.properties file in $JONAS_BASE/conf:
... carol.protocols=cmi... ...
The new horizontal replication algorithm uses a database table to keep track of current running transactions. This table is accessed from the new elected node during fail-over to detect whether or not the current transaction committed at the former local node, ensuring exactly-once semantics. The table contains only one column: the transaction identifier (txid).
In JOnAS 4.8 this table must be created manually with the following SQL command:
create TABLE ha_transactions (txid varchar(60));
This table should be located preferably in the database used by the replicated application, but it is not mandatory. If the table is not created in the database used by the replicated application, it is necessary to configure a new datasource for the database that contains this transaction table. This datasource must be configured to use the serializable transaction isolation level.
The database that holds the transaction table is accessed by the replication service with the JNDI name configured in jonas.properties.
... jonas.service.ha.datasource tx_table_ds ...
Due to the fact that the replication algorithm stores information associated with clients' transactions and that the server is not notified when a client dies, the HA service might have been storing unnecessary replication information over time. In order to automatically clean this unnecessary replication information, the HA service includes a garbage collection mechanism. It is possible to configure the number of seconds the system waits to execute this mechanism by changing the following property in the jonas.properties file:
... jonas.service.ha.timeout 600 ...
In order to configure an application for replication, the <cluster-replicated/> element must be added to the bean definition of every bean requiring high availability in the jonas-ejb-jar.xml deployment descriptor file. This element can have two possible values: true or false (default value). In addition, if the programmer wants to change the behavior of the CMI stubs (e.g., the server selection policy), it is possible to specify different distributor implementations by means of <cluster-home-distributor/> and <cluster-remote-distributor/> elements. In this case, the value corresponds to the .vm file that implements the distributor in its home and remote parts respectively. If the <cluster-replicated/> element is present without the <cluster-*-distributor/> elements, the default values are used (ClusterHomeSFSBRepDistributor.vm and ClusterRemoteSFSBRepDistributor.vm).
The following is an example description for a replicated SFSB in jonas-ejb-jar.xml file:
... <jonas-session> <ejb-name>DummySFSB</ejb-name> <jndi-name>DummySFSB</jndi-name> ... <cluster-replicated>true</cluster-replicated> <cluster-home-distributor>Dummy_HomeDistributor.vm</cluster-home-distributor> <cluster-remote-distributor>Dummy_RemoteDistributor.vm</cluster-remote-distributor> </jonas-session> ...
The <cluster-replicated/> element can also be set in the SSB or EB for
enabling the transaction checking mechanism ensuring the exactly-once semantic at fail-over
supporting the EB references replication
Note: When set in the SSB, the mechanism inhibits the load-balancing at the remote interface. After the home create() method call, all the requests are sent to the same instance.
The lock policy for the Entity Beans in a replicated application must be configured as database in the jonas-ejb-jar.xml deployment descriptor file.
The following is an example description for a replicated EB in the jonas-ejb-jar.xml:
...
<jonas-entity>
<ejb-name>MyEntitySLR</ejb-name>
<jndi-name>MyEntityHome</jndi-name>
<cluster-replicated>true</cluster-replicated>
<shared>true</shared>
<jdbc-mapping>
<jndi-name>example_ds</jndi-name>
</jdbc-mapping>
<lock-policy>database</lock-policy>
</jonas-entity>
...
The datasources used by replicated applications must be configured to use the serializable transaction isolation level.
The following is an example for a datasource configuration file for the Postgres DBMS:
... datasource.name example_ds datasource.url jdbc:postgresql://xxx.xxx.xxx.xxx:xxxx/database datasource.classname org.postgresql.Driver datasource.username jonas datasource.password datasource.mapper rdb.postgres datasource.isolationlevel serializable ...
Finally, when compiling the application that includes the replicated beans, the CMI protocol must be specified in order to generate the classes that include the replication logic.
The JOnAS administration console offers several items of information about the HA service's replication algorithm and allows the configuring of several parameters related to its behaviour. The related information and parameters include:
The name of the service.
The binded name for the MBean. The name can be changed.
The number of replicated messages sent by the algorithm to the cluster's replicas.
The average size of the replicated messages sent.
The total size of the replicated messages sent.
The current JGroups configuration file name used.
The current timeout established to clean in memory information related to SFSBs required by the algorithm. When this timeout expires, the information is garbage-collected. This avoids increasing the memory used by the algorithm. The administrator can set a different timeout if required.
-
The datasource name required by the algorithm to keep track of current running transactions (See Transaction Table Configuration section above). The default datasource is setted through the "jonas.service.ha.datasource" parameter in the "jonas.properties" configuration file, but the administrator can configure different datasources and can set here, the name of the one that will be used by the algorithm, once JOnAS has started.
![[Note]](../../resources/images/note.png)
Note It is recomended to not change the Datasource once the HA service is running.
The JMS API provides a separate domain for each messaging approach, point-to-point or publish/subscribe. The point-to-point domain is built around the concept of queues, senders and receivers. The publish/subscribe domain is built around the concept of topic, publisher and subscriber. Additionally it provides a unified domain with common interfaces that enable the use of queue and topic. This domain defines the concept of producers and consumers. The classic sample uses a very simple configuration (centralized) made of one server hosting a queue and a topic. The server is administratively configured for accepting connection requests from the anonymous user.
JMS clustering aims to offer a solution for both the scalability and the high availability for the JMS accesses. This document gives an overview of the JORAM capabilities for clustering a JMS application in the J2EE context. The load-balancing and fail-over mechanisms are described and a user guide describing how to build such a configuration is provided. Further information is available in the JORAM documentation here .
The following information will be presented:
Load balancing throw cluster topic and cluster queue. The distributed capabilities of JORAM will be examined.
How to present the JORAM HA enabling to ensure the high availability of the JORAM server.
How to build an MDB clustering architecture with both JOnAS and JORAM enabling to build an MDB based application ensuring the high availability.
Getting started :
Install and configure two JOnAS instances (see here ). The newjc tool may be used for generating the initial configuration of the JMS cluster. The tool may be run with the default inputs except for the architecture (bothWebEjb) and number of nodes (2). See here for further information about the newjc tool.
JOnAS's examples newsamplemdb and newsamplemdb2 will be used to illustrate the configuration. First they must be compiled. Go to $JONAS_ROOT/examples/src and do ant install.
Two instances of JOnAS are configured ("J1" and "J2"). Each JOnAS instance has a dedicated collocated JORAM server: server "S1" for JOnAS "J1", "S2" for "J2". Those two servers are aware of each other.
Set a JORAM distributed configuration:
-
Go to $JONAS_BASE/conf and edit the a3servers.xml file (same for the 2 instances). 2 instances are defined in the same domain network. The persistent mode is enabled.
<?xml version="1.0"?> <config <domain name="D1"/> <property name="Transaction" value="fr.dyade.aaa.util.NTransaction"/> <server id="1" name="S1" hostname="localhost"> <network domain="D1" port="16301"/> <service class="org.objectweb.joram.mom.proxies.ConnectionManager" args="root root"/> <service class="org.objectweb.joram.mom.proxies.tcp.TcpProxyService" args="16010"/> </server> <server id="2" name="S2" hostname="localhost"> <network domain="D1" port="16302"/> <service class="org.objectweb.joram.mom.proxies.ConnectionManager" args="root root"/> <service class="org.objectweb.joram.mom.proxies.tcp.TcpProxyService" args="16020"/> </server> </config> -
For each instance, edit the ra.xml embedded in the joram_for_jonas_ra.rar (by using unjar command manually or with the jonasAdmin's RA editor) and check the following element according to the a3servers.xml content
-
server id (1 or 2)
<config-property> <config-property-name>ServerId</config-property-name> <config-property-type>java.lang.Short</config-property-type> <config-property-value>1</config-property-value> </config-property> -
server name (S1 or S2)
<config-property> <config-property-name>ServerName</config-property-name> <config-property-type>java.lang.String</config-property-type> <config-property-value>s1</config-property-value> </config-property> -
hostname
<config-property> <config-property-name>HostName</config-property-name> <config-property-type>java.lang.String</config-property-type> <config-property-value>localhost</config-property-value> </config-property> -
network port (16010 or 16020)
<config-property> <config-property-name>ServerPort</config-property-name> <config-property-type>java.lang.Integer</config-property-type> <config-property-value>16010</config-property-value> </config-property> -
persistent mode
<config-property> <config-property-name>PersistentPlatform</config-property-name> <config-property-type>java.lang.Boolean</config-property-type> <config-property-value>true</config-property-value> </config-property>
-
-
For each instance, edit the joramAdmin.xml, update the connection factories definition, the user definition according to the local JORAM server configuration
-
server id (1 or 2)
<User name="anonymous" password="anonymous" serverId="1"/> -
server port number (16010 or 16020)
<ConnectionFactory className="org.objectweb.joram.client.jms.tcp.TcpConnectionFactory"> <tcp host="localhost" port="16010"/> <jndi name="JCF"/> </ConnectionFactory> <ConnectionFactory className="org.objectweb.joram.client.jms.tcp.QueueTcpConnectionFactory"> <tcp host="localhost" port="16010"/> <jndi name="JQCF"/> </ConnectionFactory> <ConnectionFactory className="org.objectweb.joram.client.jms.tcp.TopicTcpConnectionFactory"> <tcp host="localhost" port="16010"/> <jndi name="JTCF"/> </ConnectionFactory>
-
See here for more information about a JORAM distributed configuration.
A non hierarchical topic might also be distributed among many servers. Such a topic, to be considered as a single logical topic, is made of topic representatives, one per server. Such an architecture allows a publisher to publish messages on a representative of the topic. In the example, the publisher works with the representative on server 1. If a subscriber subscribed to any other representative (on server 2 in the example), it will get the messages produced by the publisher.
Load balancing of topics is very useful because it allows distributed topic subscriptions across the cluster.
 |
The following scenario and general settings are proposed:
The cluster topic is composed of two elements : mdbTopic1 defined hosted by JORAM server S1 and mdbTopic2 hosted by JORAM server S2.
The jndi name 'mdbTopic' is set for the local representative, ie mdbTopic1 for S1 et mdbTopic2 for S2.
At the server side, a MDB is listening the local representative 'mdbTopic'.
A client connects to the J1 or J2 server and sends 10 messages to the topic 'mdbTopic'.
Each message is received twice, one per cluster element.
 |
The cluster definition with the topics must be added in $JONAS_BASE/conf/joramAdmin.xml file. The connection factories and the anonymous user must be defined with the local server id and the local server port number according to the a3servers.xml content. Here only the cluster related elements are shown:
-
For the server id 1 :
<Topic name="mdbTopic1" serverId="1"> <freeReader/> <freeWriter/> <jndi name="mdbTopic"/> </Topic> <Topic name="mdbTopic2" serverId="2"> <freeReader/> <freeWriter/> <jndi name="mdbTopic2"/> </Topic> <ClusterTopic> <ClusterElement name="mdbTopic1" location="s1"/> <ClusterElement name="mdbTopic2" location="s2"/> <jndi name="clusterMdbTopic"/> </ClusterTopic> -
For the server id 1 :
<Topic name="mdbTopic1" serverId="1"> <freeReader/> <freeWriter/> <jndi name="mdbTopic1"/> </Topic> <Topic name="mdbTopic2" serverId="2"> <freeReader/> <freeWriter/> <jndi name="mdbTopic"/> </Topic> <ClusterTopic> <ClusterElement name="mdbTopic1" location="s1"/> <ClusterElement name="mdbTopic2" location="s2"/> <jndi name="clusterMdbTopic"/> </ClusterTopic>
The joramAdmin.xml file has to be loaded when all cluster members are started since some remote cluster elements are defined. An alternative consists in splitting the configuration into two different files joramAdmin-local.xml and joramAdmin-cluster.xml, the first one containing only the local elements and the second one, both local and remote elements. At the JOnAS starting, a script could copy the right file to joramAdmin.xml according to the others members presence (joramAdmin-local.xml if it's the first member which starts and joramAdmin-cluster.xml if all the cluster members are started).
Deploy the application, for example, create a deploy.sh file:
#!/bin/ksh
export JONAS_BASE=$PWD/jb1
cp $JONAS_ROOT/examples/output/ejbjars/newsamplemdb.jar $JONAS_BASE/ejbjars/
jonas admin -a newsamplemdb.jar -n node1
export JONAS_BASE=$PWD/jb2
cp $JONAS_ROOT/examples/output/ejbjars/newsamplemdb.jar $JONAS_BASE/ejbjars/
jonas admin -a newsamplemdb.jar -n node2
jclient newsamplemdb.MdbClient
Something similar to this should appear in the client console :
ClientContainer.info : Starting client...
JMS client: tcf = TCF:localhost-16010
JMS client: topic = topic#1.1.1026
JMS client: tc = Cnx:#0.0.1026:5
MDBsample is Ok
In addition, the following should appear on each JOnAS instance console:
Message received: Message6
MdbBean onMessage
Message received: Message7
MdbBean onMessage
Message received: Message8
The fact that each message appears on the two different JOnAS servers consoles shows the messages broadcasting between the topic elements.
Globally, the load balancing in the context of queues may be meaningless in comparison of load balancing topic. It would be a bit like load balancing a stateful session bean instance (which just requires failover). But the JORAM distributed architecture enables :
equilibrating the load of the queue access between several JORAM server nodes, it's a queue load-balancing at the server side.
load-balancing the load at the client side.
Here is a diagram of what is going to happen for the Queue and the message:
 |
A load balancing message queue may be needed for a high rate of messages. A clustered queue is a cluster of queues exchanging messages depending on their load. The example has a cluster of two queues. A heavy producer accesses its local queue and sends messages. It quickly becomes loaded and decides to forward messages to the other queue of its cluster which is not under heavy load.
For this case some parameters must be set:
period: period (in ms) of activation of the load factor evaluation routine for a queue
producThreshold: number of messages above which a queue is considered loaded, a load factor evaluation launched, messages forwarded to other queues of the cluster
consumThreshold: number of pending "receive" requests above which a queue will request messages from the other queues of the cluster
autoEvalThreshold: set to "true" for requesting an automatic revaluation of the queues' thresholds values according to their activity
waitAfterClusterReq: time (in ms) during which a queue that requested something from the cluster is not authorized to do it again
For further information, see the JORAM documentation here .
The scenario for Queue is similar to the topic one. A client sent messages to a queue in S1. MDB gets messages from each local cluster queue representative. After having sent a burst of messages to the server S1, the load distribution should occur and message should be moved to S2.
The Queue definition in $JONAS_BASE/conf/joramAdmin.xml file is as following :
-
For server 1
<Queue name="mdbQueue1" serverId="1" className="org.objectweb.joram.mom.dest.ClusterQueue"> <freeReader/> <freeWriter/> <property name="period" value="10000"/> <property name="producThreshold" value="50"/> <property name="consumThreshold" value="2"/> <property name="autoEvalThreshold" value="false"/> <property name="waitAfterClusterReq" value="1000"/> <jndi name="mdbQueue"/> </Queue> <Queue name="mdbQueue2" serverId="2" className="org.objectweb.joram.mom.dest.ClusterQueue"> <freeReader/> <freeWriter/> <property name="period" value="10000"/> <property name="producThreshold" value="50"/> <property name="consumThreshold" value="2"/> <property name="autoEvalThreshold" value="false"/> <property name="waitAfterClusterReq" value="1000"/> <jndi name="mdbQueue2"/> <ClusterQueue> <ClusterElement name="mdbQueue1" location="s1"/> <ClusterElement name="mdbQueue2" location="s2"/> <jndi name="mdbQueueCluster"/> </ClusterQueue> -
For server 2
<Queue name="mdbQueue1" serverId="1" className="org.objectweb.joram.mom.dest.ClusterQueue"> <freeReader/> <freeWriter/> <property name="period" value="10000"/> <property name="producThreshold" value="50"/> <property name="consumThreshold" value="2"/> <property name="autoEvalThreshold" value="false"/> <property name="waitAfterClusterReq" value="1000"/> <jndi name="mdbQueue1"/> </Queue> <Queue name="mdbQueue2" serverId="2" className="org.objectweb.joram.mom.dest.ClusterQueue"> <freeReader/> <freeWriter/> <property name="period" value="10000"/> <property name="producThreshold" value="50"/> <property name="consumThreshold" value="2"/> <property name="autoEvalThreshold" value="false"/> <property name="waitAfterClusterReq" value="1000"/> <jndi name="mdbQueue"/> <ClusterQueue> <ClusterElement name="mdbQueue1" location="s1"/> <ClusterElement name="mdbQueue2" location="s2"/> <jndi name="mdbQueueCluster"/> </ClusterQueue>
Run the sample
The procedure is similar to the topic example described above, just use the newsamplemdb2 example rather than newsample one.
The load-balancing is done at the client side. A server is selected randomly among the cluster members at the first message sending or through the 'location' java property. And then, for a given client, all the messages are sent to the same server unless the java property resetting.
 |
For setting the load-balancing at the client side, the client application must use a clustered connection factory that embeds the network connection parameters of the cluster members. This factory must be registered in the JORAM's distributed JNDI for ensuring that the client gets an up to date object. The main parameters are given below :
At first, the a3servers.xml file must enhanced with the JORAM's jndi service as following :
<?xml version="1.0"?>
<config>
<domain name="D1"/>
<property name="Transaction" value="fr.dyade.aaa.util.NTransaction"/>
<server id="0" name="s0" hostname="localhost">
<network domain="D1" port="16301"/>
<service class="org.objectweb.joram.mom.proxies.ConnectionManager"
args="root root"/>
<service class="org.objectweb.joram.mom.proxies.tcp.TcpProxyService"
args="16010"/>
<service class="fr.dyade.aaa.jndi2.distributed.DistributedJndiServer"
args="16401 0 1"/>
</server>
<server id="1" name="s1" hostname="localhost">
<network domain="D1" port="16302"/>
<service class="org.objectweb.joram.mom.proxies.ConnectionManager"
args="root root"/>
<service class="org.objectweb.joram.mom.proxies.tcp.TcpProxyService"
args="16020"/>
<service class="fr.dyade.aaa.jndi2.distributed.DistributedJndiServer"
args="16402 1 0"/>
</server>
</config>
Only the JMS objects must be registered in the JORAM's jndi. The standard routing mechanism is used through a jndi.properties file put in each $JONAS_BASE/conf directory :
-
port number (16401 or 16402)
java.naming.factory.url.pkgs org.objectweb.jonas.naming:fr.dyade.aaa.jndi2 scn.naming.factory.host localhost scn.naming.factory.port 16402
The port number must be adapted according to the local server configuration (16401 for S1 and 16402 for S2). The 'scn' prefix is defined for identifying the objects to bind or to lookup in this registry.
The clustered connection factories are defined in the $JONAS_BASE/conf/joramAdmin.xml file as following :
<ConnectionFactory name="JQCF1" className="org.objectweb.joram.client.jms.tcp.QueueTcpConnectionFactory">
<tcp host="localhost"
port="16010"/>
<jndi name="scn:comp/JQCF1"/>
</ConnectionFactory>
<ConnectionFactory name="JQCF2" className="org.objectweb.joram.client.jms.tcp.QueueTcpConnectionFactory">
<tcp host="localhost"
port="16020"/>
<jndi name="scn:comp/JQCF2"/>
</ConnectionFactory>
<ClusterCF>
<ClusterElement name="JQCF1" location="s1"/>
<ClusterElement name="JQCF2" location="s2"/>
<jndi name="scn:comp/clusterJQCF"/>
</ClusterCF>
The 'scn:comp/' prefix in the jndi name indicates that the object must be bound in the JORAM's jndi.
The cluster queue is defined in the $JONAS_BASE/conf/joramAdmin.xml file :
<Queue name="mdbQueue0" serverId="1"
className="org.objectweb.joram.mom.dest.ClusterQueue">
<freeReader/>
<freeWriter/>
<jndi name="scn:comp/mdbQueue1"/>
</Queue>
<Queue name="mdbQueue1" serverId="2"
className="org.objectweb.joram.mom.dest.ClusterQueue">
<freeReader/>
<freeWriter/>
<jndi name="scn:comp/mdbQueue2"/>
</Queue>
<ClusterQueue>
<ClusterElement name="mdbQueue1" location="s1"/>
<ClusterElement name="mdbQueue2" location="s2"/>
<jndi name="scn:comp/mdbQueue"/>
</ClusterQueue>
Note that the cluster queue definition is symetric accross the cluster members. The well known jndi name is set on the cluster object (and not in the local representative as for the topic cluster).
Note that same for the topic declaration, the joramAdmin.xml file has to be loaded when all cluster members are started since some remote cluster elements are defined. An alternative consists in splitting the configuration into two different files joramAdmin-local.xml and joramAdmin-cluster.xml, the first one containing only the local elements and the second one, both local and remote elements. At the JOnAS starting, a script could copy the right file to joramAdmin.xml according to the others members presence (joramAdmin-local.xml if it's the first member which starts and joramAdmin-cluster.xml if all the cluster members are started).
The message driven bean must be configured with the queue registered in the JORAM jndi ('scn:/comp' selector). Edit the deployment descriptor file (ejb-jar.xml) :
<message-driven>
<description>Describe here the message driven bean Mdb</description>
<display-name>Message Driven Bean Mdb</display-name>
<ejb-name>Mdb</ejb-name>
<ejb-class>newsamplemdb2.MdbBean</ejb-class>
<messaging-type>javax.jms.MessageListener</messaging-type>
<transaction-type>Container</transaction-type>
<message-destination-type>javax.jms.Queue</message-destination-type>
<activation-config>
<activation-config-property>
<activation-config-property-name>destination</activation-config-property-name>
<activation-config-property-value>scn:comp/mdbQueue</activation-config-property-value>
</activation-config-property>
<activation-config-property>
<activation-config-property-name>destinationType</activation-config-property-name>
<activation-config-property-value>javax.jms.Queue</activation-config-property-value>
</activation-config-property>
<activation-config-property>
<activation-config-property-name>subscriptionDurability</activation-config-property-name>
<activation-config-property-value>NonDurable</activation-config-property-value>
</activation-config-property>
</activation-config>
</message-driven>
The client must lookup the clustered objects in the JORAM's jndi by using the 'scn:/comp' selector.
static String queueName = "scn:comp/mdbQueue";
static String conFactName = "scn:comp/clusterJQCF";
Context ictx = new InitialContext();
ConnectionFactory qcf = (ConnectionFactory) ictx.lookup(conFactName );
Queue queue = (Queue) ictx.lookup(queueName);
The connection creation, session creation and producer are quite classic:
Connection qc = qcf.createConnection();
Session session = qc.createSession(false, Session.AUTO_ACKNOWLEDGE);
MessageProducer qp = session.createProducer(queue);
A server is chosen at the first message sending. A switch may be forced through the resetting of the 'location' java property. Below a new server election is requested for each odd iteration.
TextMessage message;
for (int i = 0; i < 10; i++) {
message = session.createTextMessage();
message.setText("Msg "+i);
qp.send(message);
System.out.println("location=" + System.getProperty("location"));
if (i%2 == 0) {
System.setProperty("location", "");
}
}
 |
An HA server is actually a group of servers, one of which is the master server that coordinates the other slave servers. An external server that communicates with the HA server is actually connected to the master server.
Each replicated JORAM server executes the same code as a standard server except for the communication with the clients.
In the example, the collocated clients use a client module (newsamplemdb). If the server replica is the master, then the connection is active enabling the client to use the HA JORAM server. If the replica is a slave, then the connection opening is blocked until the replica becomes the master.
Several files must be changed to create a JORAM HA configuration:
A clustered server is defined by the element "cluster". A cluster owns an identifier and a name defined by the attributes "id" and "name" (exactly like a standard server). Two properties must be defined:
"Engine" must be set to "fr.dyade.aaa.agent.HAEngine" which is the class name of the engine that provides high availability.
"nbClusterExpected" defines the number of replicas that must be connected to the group communication channel used before this replica starts. By default it is set to 2. If there are more than two clusters, this specification must be inserted in the configuration file. If there are two clusters, this specification is not required.
In the case of one server and one replica, the value must be set to 1.
<?xml version="1.0"?/>
<config>
<domain name="D1"/>
<property name="Transaction" value="fr.dyade.aaa.util.NullTransaction"/>
<cluster id="0" name="s0">
<property name="Engine" value="fr.dyade.aaa.agent.HAEngine" />
<property name="nbClusterExpected" value="1" />
For each replica, an element "server" must be added. The attribute "id" defines the identifier of the replica inside the cluster. The attribute "hostname" gives the address of the host where the replica is running. The network is used by the replica to communicate with external agent servers, i.e., servers located outside of the cluster and not replicas.
This is the entire configuration for the a3servers.xml file of the first JOnAS instance jb1:
<?xml version="1.0"?>
<config<
<domain name="D1"/>
<property name="Transaction" value="fr.dyade.aaa.util.NullTransaction"/>
<cluster id="0" name="s0">
<property name="Engine" value="fr.dyade.aaa.agent.HAEngine" />
<property name="nbClusterExpected" value="1" />
<server id="0" hostname="localhost">
<network domain="D1" port="16300"/>
<service class="org.objectweb.joram.mom.proxies.ConnectionManager" args="root root"/>
<service class="org.objectweb.joram.mom.proxies.tcp.TcpProxyService" args="16010"/>
<service class="org.objectweb.joram.client.jms.ha.local.HALocalConnection"/>
</server>
<server id="1" hostname="localhost">
<network domain="D1" port="16301"/>
<service class="org.objectweb.joram.mom.proxies.ConnectionManager" args="root root"/>
<service class="org.objectweb.joram.mom.proxies.tcp.TcpProxyService" args="16020"/>
<service class="org.objectweb.joram.client.jms.ha.local.HALocalConnection"/>
</server>
</cluster>
</config>
The cluster id = 0 and the name S0. It is exactly the same file for the second instance of JOnAS.
Here is the joramAdmin.xml file configuration:
<?xml version="1.0"?>
<JoramAdmin>
<AdminModule>
<collocatedConnect name="root" password="root"/>
</AdminModule>
<ConnectionFactory className="org.objectweb.joram.client.jms.ha.tcp.HATcpConnectionFactory">
<hatcp url="hajoram://localhost:16010,localhost:16020" reliableClass="org.objectweb.joram.client.jms.tcp.ReliableTcpClient"/>
<jndi name="JCF"/>
</ConnectionFactory>
<ConnectionFactory className="org.objectweb.joram.client.jms.ha.tcp.QueueHATcpConnectionFactory">
<hatcp url="hajoram://localhost:16010,localhost:16020" reliableClass="org.objectweb.joram.client.jms.tcp.ReliableTcpClient"/>
<jndi name="JQCF"/>
</ConnectionFactory>
<ConnectionFactory className="org.objectweb.joram.client.jms.ha.tcp.TopicHATcpConnectionFactory">
<hatcp url="hajoram://localhost:16010,localhost:16020" reliableClass="org.objectweb.joram.client.jms.tcp.ReliableTcpClient"/>
<jndi name="JTCF"/>
</ConnectionFactory>
Each connection factory has its own specification. One is in case of the Queue, one for Topic, and one for no define arguments. Each time the hatcp url must be entered, the url of the two instances. In the example, it is localhost:16010 and localhost:16020. It allows the client to change the instance when the first one is dead.
After this definition the user, the queue and topic can be created.
First, in order to recognize the cluster, a new parameter must be declared in these files.
<config-property>
<config-property-name>ClusterId</config-property-name>
<config-property-type>java.lang.Short</config-property-type>
<config-property-value>0</config-property-value>
</config-property>
Here the name is not really appropriate but in order to keep some coherence this name was used. In fact it represents a replica so it would have been better to call it replicaId.
Consequently, for the first JOnAS instance, copy the code just above. For the second instance, change the value to 1 (in order to signify this is another replica).
First launch the two JOnAS bases. Create a runHa.sh file in which the following code will be added:
export JONAS_BASE=$PWD/jb1
export CATALINA_BASE=$JONAS_BASE
rm -f $JONAS_BASE/logs/*
jonas start -win -n node1 -Ddomain.name=HA
Then do the same for the second JOnAS base. After that launch the script.
One of the two JOnAS bases (the one which is the slowest) will be in a waiting state when reading the joramAdmin.xml
JoramAdapter.start : - Collocated JORAM server has successfully started.
JoramAdapter.start : - Reading the provided admin file: joramAdmin.xml
whereas the other one is launched successfully.
Then launch (through a script or not) the newsamplemdb example:
jclient -cp /JONAS_BASE/jb1/ejbjars/newsamplemdb.jar:/JONAS_ROOT/examples/classes -carolFile clientConfig/carol.properties newsamplemdb.MdbClient
Messages are sent on the JOnAS base which was launched before. Launch it again and kill the current JOnAS. The second JOnAS will automatically wake up and take care of the other messages.
This is a proposal for building an MDB clustering based application.
This is like contested Queues. i.e., there is more than one receiver on different machines receiving from the queue. This load balances the work done by the queue receiver, not the queue itself.
The HA mechanism can be mixed with the load balancing policy based on clustered destinations. The load is balanced between several HA servers. Each element of a clustered destination is deployed on a separate HA server.
 |
Here is the supposed configuration (supposed because it has not been verifed).
 |
The configuration must now be tested, as follows:
First make JA1 crash and verify that messages are spread between JB1 and JB2.
Then make JB2 crash and verify that messages are spread between JA1 and JA2.
Finally make JA1 and JB2 crash and verify that messages are spread between JA2 and JB1.
A domain represents an administration perimeter which is under the control of an administration authority. It provides at least one common administration point for the elements in the domain.
A JOnAS domain may contain:
-
JOnAS instances
-
groups of instances called clusters
-
cluster daemons, elements used for the remote control of instances and clusters
A common administration point is represented by a JOnAS instance having a particular configuration and playing the role of master. A master has the knowledge of the domain topology and allows executing administration operations on the rest of the servers and on the clusters. It also allows the monitoring of the domain elements.
The administered elements are identified by their names, that have to be unique within the domain, and the domain name.
Names can be defined in a static way, through the
domain.xml configuration file, or dynamically, by
starting new elements in the domain. For example, when starting a JOnAS
instance, the administrator can specify the server
name using the -n option and the domain
name by setting the domain.name environment
property. The uniqueness of the starting server's name is enforced by
the discovery service.
A domain configuration consists in the domain topology - the description of the elements composing the domain, and the state of the elements in the domain, as viewed from the common administration point.
Before starting the master, the administrator can define an initial
domain topology using the domain.xml configuration
file.
The domain configuration dynamically evolves by starting or stopping servers and by creating or removing clusters in the domain.
The first step is to choose a name for the domain and to choose a server to represent the common administration point. This server must be configured as a master by setting to true the jonas.master property. Also, to allow dynamic domain management, add the discovery service in the JOnAS services list (jonas.services property).
The domain name is not a configuration property for the master (neither for any server in the domain), but it has to be specified when starting the master.
Before starting the master, the administrator can define the
domain's initial topology by editing the domain.xml configuration file.
This step is optional. It consists in defining the domain elements
using the domain.xml configuration file located in
the master's configuration directory. If the administrator has no specific
configuration needs, it should at least check the name element,
and set its value to the chosen name. That file
can also be used to define a default user name and password to use when
connecting to servers and cluster daemons. Moreover, the administrator
can choose to remove the domain.xml file.
The elements that can be defined in domain.xml are:
-
server elements: allow to define a server in the domain, or a server in a cluster. A server has a name, a description, a location and optionally a user name and password as well as an associated cluster daemon. The location can be represented by a list of JMX remote connector server URLs.
-
cluster elements: allows to group servers in a logical cluster.
-
cluster daemon elements: allows to define a cluster daemon in the domain. A cluster daemon element has a name, a description, a location and optionally a user name and password. The location can be represented by a list of JMX remote connector server URLs.
Start the master in the domain:
jonas start -n masterName -Ddomain.name=domainName
Note that the domain name is specified by setting a
domain.name environment property.
Once started, the administrator can manage and monitor the following elements in the domain through JonasAdmin, or another JMX based administration application, running on the master:
-
servers declared in the domain.xml file.
-
other servers already started in the domain having the discovery service enabled.
-
clusters declared in the domain.xml file.
-
clusters detected by the administration framework
-
cluster daemons declared in the domain.xml file.
The intent of the cluster daemon is to enable the remote control of the JOnAS clustered instances through a JMX interface.
In a cluster configuration, the cluster daemon is the bootstrap of the JOnAS instances.
There is at least one cluster daemon instance per machine.

In the same manner as a classic JOnAS instance, the cluster daemon reads its configuration in a directory pointed to by a JONAS_BASE variable (or JONAS_ROOT if JONAS_BASE is not set). All the default JONAS_BASE subdirectories and files are not required; the mandatory ones are:
| element | description |
|---|---|
| $JONAS_BASE/conf | Configuration directory |
| $JONAS_BASE/logs | Log directory |
| $JONAS_BASE/conf/carol.properties | Carol configuration file describing the protocol and its parameters (used for the JMX interface) |
| $JONAS_BASE/conf/trace.properties | Trace/Error log configuration file |
| $JONAS_BASE/conf/jonas.properties | This file must be present for enabling the cluster daemon starting but its content is not read, the file can be empty |
| $JONAS_BASE/conf/clusterd.xml | Cluster daemon configuration file, lists the local JOnAS instances and describes their environment (see below) |
The JOnAS instances controlled by a cluster daemon are configured in the
clusterd.xml
file.
<?xml version="1.0"?>
<cluster-daemon xmlns="http://www.objectweb.org/jonas/ns"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.objectweb.org/jonas/ns
http://www.objectweb.org/jonas/ns/jonas-clusterd_4_8.xsd">
<name>cd1</name>
<domain-name>domainSample</domain-name>
<jonas-interaction-mode>loosely-coupled</jonas-interaction-mode>
<server>
<name>node1</name>
<description>Web instance</description>
<java-home>/usr/java/jdk-ia32/sun/j2sdk1.4.2_10</java-home>
<jonas-root>/home/pelletib/pkg/jonas_root_sb48</jonas-root>
<jonas-base>/home/pelletib/tmp/newjc48/jb1</jonas-base>
<xprm></xprm>
<auto-boot>false</auto-boot>
<jonas-cmd></jonas-cmd>
</server>
...
</cluster-daemon>
| element | description |
|---|---|
| name | Cluster daemon instance name. Used for building the connector url. |
| domain-name | Domain name to use for launching the JOnAS instance when it is not specified in the start command |
| jonas-interaction-mode |
Starting mode of the JOnAS instances:
loosely-coupled
corresponds to background and
tighly-coupled
corresponds to foreground
|
| server/name | Name of the JOnAS instance |
| server/description | Description of the JOnAS instance |
| server/java-home | JDK home directory to use for launching the JOnAS instance |
| server/jonas-root | JOnAS binaries directory to use for launching the JOnAS instance |
| server/jonas-base | JOnAS configuration directory to use for launching the JOnAS instance |
| server/xprms | JVM parameters to set when launching the JOnAS instance |
| server/auto-boot | If true, start the JOnAS instance when launching the cluster daemon |
| server/jonas-cmd | Optional parameter. If set, specifies the script to use for starting/stopping the JOnAS instance. This user script can set the required environnement and perform some pre or post processing. By default, the jonas command is used. |
The cluster daemons must be specified and associated to the JOnAS instances in the
domain.xml
file for permitting the remote control of the cluster.
...
<cluster-daemon>
<name>cd1</name>
<description>cluster daemon 1</description>
<location>
<url>service:jmx:rmi://host/jndi/rmi://host:port/jrmpconnector_cd</url>
</location>
</cluster-daemon>
...
<server>
<name>node1</name>
<cluster-daemon>cd1</cluster-daemon>
...
</server>
...
The JMX remote url of the cluster daemon adheres to the following syntax:
service:jmx:rmi://
host
/jndi/rmi://
host
:
port
/
protocol
connector_
name
with the following meanings:
- host
ip alias or ip address of the machine that hosts the cluster daemon (by default localhost, can be overridden through the carol.properties file)
- port
tcp listen port of the registry embedded in the cluster daemon (by default 1806, can be overridden through the carol.properties file)
- protocol
protocol used for accessing the JMX interface (by default irmi, can be overridden through the carol.properties file)
- name
cluster daemon instance name (defined in the clusterd.xml file)
The cluster daemon is started using the command
jclusterd
. The possible options are:
| option | description |
|---|---|
| start | Start the cluster daemon. |
| stop | Stop the cluster daemon. |
| -DdomainName | Domain name to use for starting the JOnAS instance. This value is used when it is defined both here and in the clusterd.xml file. |
| -carolFile <my-carol.properties> | Path to the carol.properties file to use. If not specified, the file is loaded from $JONAS_BASE/conf. If the file is not found, the default values (localhost, 1806, irmi) are used. |
| -confFile <my-clusterd.xml> | Path to the clusterd.xml file to load. If not specified, the file is loaded from $JONAS_BASE/conf. |
The cluster daemon provides a JMX interface that enables control of the JOnAS instances. The following operations are available:
| Operation | Description |
|---|---|
| String getServersList() | Return the list of JOnAS instances |
| int pingJOnAS(String name) | Ping a JOnAS instance identified by its name |
| void startJOnAS(String name) | Start a JOnAS instance identified by its name |
| String startAllJOnAS(String domainName, String prm) |
Start all the JOnAS instances known in the cluster daemon configuration. The parameter
domainName
(optional) enables the ability to specifiy the domain name. The parameter
prm
(optional) enables the ability to set some JVM parameters.
|
| void stopJOnAS(String name) | Stop a JOnAS instance identified by its name |
| String stopAllJOnAS() | Stop all the JOnAS instances known in the cluster daemon configuration |
| String getJavaHome4Server(String name) | Get the JAVA_HOME defined for a JOnAS server |
| String getJonasRoot4Server(String name) | Get the JONAS_ROOT defined for a JOnAS server |
| String getJonasBase4Server(String name) | Get the JONAS_BASE defined for a JOnAS server |
| void reloadConfiguration() | Reload the configuration file of the cluster daemon |
| void addServer(String name, String description, String javaHome, String jonasRoot, String jonasBase) | Add a definition of a JOnAS instance to the cluster daemon configuration. The change is saved in the configuration file. |
| void removeServer(String name) | Remove a definition of a JOnAS instance in the cluster daemon configuration. The change is saved in the configuration file. |
| void modifyServer(String name, String description, String javaHome, String jonasRoot, String jonasBase) | Modify the definition of a JOnAS instance in the cluster daemon configuration. The change is saved in the configuration file. |
EasyBeans is configured with the help of an easy-to-understand XML configuration file.
The following is an example of an EasyBeans XML configuration file:
<?xml version="1.0" encoding="UTF-8"?>
<easybeans xmlns="http://org.ow2.easybeans.server">
<!-- Define components that will be started at runtime -->
<components>
<!-- RMI/JRMP will be used as protocol layer -->
<rmi>
<protocol name="jrmp" port="1099" hostname="localhost" />
</rmi>
<!-- Start a transaction service -->
<tm />
<!-- Start a JMS provider -->
<jms port="16030" hostname="localhost">
<topic>dummyTopic</topic>
</jms>
<!-- Creates an embedded HSQLDB database -->
<hsqldb port="9001" dbName="jdbc_1">
<user name="easybeans" password="easybeans" />
</hsqldb>
<hsqldb port="9002" dbName="jdbc_2">
<user name="easybeans" password="easybeans" />
</hsqldb>
<!-- Add mail factories -->
<mail>
<!-- Authentication ?
<auth name="test" password="test" />
-->
<session name="javax.mail.Session factory example" jndiName="mailSession_1">
<!-- Example of properties -->
<property name="mail.debug" value="false" />
</session>
<mimepart name="javax.mail.internet.MimePartDataSource factory example" jndiName="mailMimePartDS_1">
<subject>How are you ?</subject>
<email type="to">john.doe@example.org</email>
<email type="cc">jane.doe@example.org</email>
<!-- Example of properties -->
<property name="mail.debug" value="false" />
</mimepart>
</mail>
<!-- Creates a JDBC pool with jdbc_1 JNDI name -->
<jdbcpool jndiName="jdbc_1" username="easybeans"
password="easybeans"
url="jdbc:hsqldb:hsql://localhost:9001/jdbc_1"
driver="org.hsqldb.jdbcDriver" />
<!-- Creates a JDBC pool with jdbc_2 JNDI name -->
<jdbcpool jndiName="jdbc_2" username="easybeans"
password="easybeans"
url="jdbc:hsqldb:hsql://localhost:9002/jdbc_2"
driver="org.hsqldb.jdbcDriver" />
<!-- Start smartclient server with a link to the rmi component-->
<smart-server port="2503" rmi="#rmi" />
</components>
</easybeans>
By default, an easybeans-default.xml file is
used. To change the default configuration, the user must provide a file
named easybeans.xml, which is located at
classloader/CLASSPATH.
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
The namespace used is http://org.ow2.easybeans.server. |
Each element defined inside the
<components> element is a component.
Note that some elements are required only for the standalone mode. JMS, RMI, HSQL, and JDBC pools are configured through JOnAS server when EasyBeans runs inside JOnAS.
The RMI configuration is done using the
<rmi> element.
To run EasyBeans with multiple protocols, the
<protocol> element can be added more than
once.
The hostname and port attributes are configurable.
Protocols could be "jrmp, jeremie, iiop, cmi". The default is jrmp.
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
Some protocols may require libraries that are not packaged by default in EasyBeans. |
The Transaction Component is defined by the
<tm> element.
A timeout attribute, which is the transaction
timeout (in seconds), can be defined on this element. The default is 60
seconds.
The implementation provided by the JOTM objectweb project is the default implementation.
The JMS component is used for JMS Message Driven Beans. Attributes are the port number and the hostname.
Also, the workmanager settings can be defined: minThreads, maxThreads and threadTimeout. The values are printed at the EasyBeans startup.
The default implementation is the implementation provided by the JORAM objectweb project.
EasyBeans can run an embedded database. Available attributes are
the port number and the database name. The
<hsqldb> may be duplicated in order to run
several HSQLDB instances.
Users are defined through the <user>
element.
This component allows the JDBC datasource to be bound into JNDI.
The jndi name used is provided by the jndiName
attribute.
Required attributes are username,
password, url and
driver.
Optional attributes are poolMin,
poolMax and pstmtMax. This
component provides the option to set the minimum size of the pool, the
maximum size, and the size of the prepared statement cache.
Mails can be sent by using the mail component that provides either Session or MimePartDataSource factories.
This component is used by the Smart JNDI factory on the client side. This allows the client to download missing classes. The client can be run without a big jar file that provides all the classes. Classes are loaded on demand.
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
Refer to the Chapter titled, Smart JNDI Factory, for more information about this feature. |
This configuration file can be extended to create and set properties on other classes.
A mapping file named easybeans-mapping.xml
provides the information that rmi is the CarolComponent, tm is the JOTM
component, and jms is the Joram component. This file is located in the
org.objectweb.easybeans.server package.
The following is an extract of the
easybeans-mapping.xml file.
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
The mapping file is using a schema available at http://easybeans.ow2.org/xml/ns/xmlconfig/xmlconfig-mapping_10.xsd |
<?xml version="1.0" encoding="UTF-8"?>
<xmlconfig-mapping xmlns="http://easybeans.ow2.org/xml/ns/xmlconfig"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://easybeans.ow2.org/xml/ns/xmlconfig
http://easybeans.ow2.org/xml/ns/xmlconfig/xmlconfig-mapping_1_0.xsd">
<class name="org.ow2.easybeans.server.ServerConfig" alias="config">
<attribute name="shouldWait" alias="wait" />
<attribute name="useMBeans" alias="mbeans" />
<attribute name="useNaming" alias="naming" />
<attribute name="initJACC" alias="jacc" />
<attribute name="directoryScanningEnabled" alias="scanning" />
<attribute name="startJMXConnector" alias="connector" />
<attribute name="registerDeployerMBean" alias="deployer" />
<attribute name="registerJ2EEServerMBean" alias="j2eeserver" />
</class>
<class name="org.ow2.easybeans.component.Components"
alias="components" />
<class name="org.ow2.easybeans.component.util.Property"
alias="property" />
<package name="org.ow2.easybeans.component.carol">
<class name="CarolComponent" alias="rmi" />
<class name="Protocol" alias="protocol">
<attribute name="portNumber" alias="port" />
</class>
</package>
<class name="org.ow2.easybeans.component.cmi.CmiComponent" alias="cmi">
<attribute name="serverConfig" alias="config" />
</class>
<class
name="org.ow2.easybeans.component.smartclient.server.SmartClientEndPointComponent"
alias="smart-server">
<attribute name="portNumber" alias="port" />
<attribute name="registryComponent" alias="rmi" />
</class>
<class name="org.ow2.easybeans.component.jotm.JOTMComponent"
alias="tm" />
<class name="org.ow2.easybeans.component.joram.JoramComponent" alias="jms">
<attribute name="topic" isList="true" getter="getTopics" setter="setTopics" element="true"/>
</class>
<class
name="org.ow2.easybeans.component.jdbcpool.JDBCPoolComponent"
alias="jdbcpool" />
<package name="org.ow2.easybeans.component.hsqldb">
<class name="HSQLDBComponent" alias="hsqldb">
<attribute name="databaseName" alias="dbName" />
<attribute name="portNumber" alias="port" />
</class>
<class name="User" alias="user">
<attribute name="userName" alias="name" />
</class>
</package>
<package name="org.ow2.easybeans.component.quartz">
<class name="QuartzComponent" alias="timer" />
</package>
<package name="org.ow2.easybeans.component.mail">
<class name="MailComponent" alias="mail" />
<class name="Session" alias="session">
<attribute name="JNDIName" alias="jndiName" />
</class>
<class name="MimePart" alias="mimepart">
<attribute name="subject" element="true" />
<attribute name="JNDIName" alias="jndiName" />
</class>
<class name="MailAddress" alias="email" element-attribute="name" />
<class name="Auth" alias="auth">
<attribute name="username" alias="name" />
</class>
</package>
</xmlconfig-mapping>
![[Note]](../../resources/images/note.png) |
Note |
|---|---|
|
This mapping file is referenced by the easybeans configuration
file using the XML namespace :
xmlns="http://org.ow2.easybeans.server" Each element configured within this namespace will use the
mapping done in the |
Users can define their own mapping by providing a file in a
package. The name of the the file must be
easybeans-mapping.xml or
element-mapping.xml.
Example: For the element <easybeans
xmlns="http://org.ow2.easybeans.server">, the resource
searched in the classloader is
org/ow2/easybeans/server/easybeans-mapping.xml. And
for an element <pool:max>2</pool:max> with
xmlns:pool="http://org.ow2.util.pool.impl", the resource searched will
be org/ow2/util/pool/impl/easybeans-mapping.xml or
org/ow2/util/pool/impl/pool-mapping.xml.
- Axis
Java platform for creating and deploying web services applications
- CAROL
Library allowing the use of different RMI implementations.
- CMI
(Clustered Method Invocation) is the JOnAS cluster protocol for high availability, load-balancing and fail-over
- EasyBeans
An Open source and lightweight EJB3 container that can be embedded in JOnAS and other application servers. It is an OW2 project.
- EIS
Enterprise Information Systems
- EJB
Enterprise JavaBeans technology is the server-side component architecture for the Java Platform, Enterprise Edition (Java EE). EJB technology enables rapid development of distributed, transactional, secure and portable applications based on Java technology.
- Hibernate
A Java-based object-relational mapping and persistence framework.
- IIOP
Inter-operable Internet Object Protocol. It is the CORBA RPC standard protocol on TCP/IP.
- JAAS
The Java Authentication and Authorization Service is a set of APIs that enable services to authenticate and enforces access controls upon users.
- JACC
Java Authorization Contract for Containers
- Jakarta Commons Logging
Wrapper around a variety of logging API implementations.
- Java EE
Java Platform, Enterprise Edition. A standard for developing portable, robust, scalable and secure server-side Java applications.
- JAXP
Java API for XML Processing. Provides the validating and parsing capabilities for XML documents.
- JAXR
Java API for XML Registries. Defines a standard API for Java platform applications to access and programmatically interact with different kinds of XML-based metadata registries.
- JAX-RPC
Java APIs for XML based RPC.
- JAX-WS
Java API for XML-based Web Services. A Java programming language API for creating web services.
- J2CA
J2EE Connector Architecture is a standard for facilitating the integration of application servers with heterogeneous Enterprise Information Systems (EISs).
- J2EE
Java 2 Platform, Enterprise Edition. A standard for developing portable, robust, scalable and secure server-side Java applications up to version 1.5 of the Java Platform.
- JDBC
Java Database Connectivity. The JDBC API provides a call-level API for SQL-based database access.
- JDK
The Java Development Kit is set of Java tools (compiler, jvm, library ...) for developing Java programs.
- JDO
The Java Data Objects API is a standard interface-based Java model abstraction for persistence.
- Jetty
A pure java open-source, standards-based, web server implementation.
- JGroups
A toolkit for reliable multicast communication.
- JMS
Java Message Service is a Java Message Oriented Middleware (MOM) API.
- JMX
Java Management Extensions. A Java technology that supplies tools for managing and monitoring applications.
- JNDI
Java Naming Directory Interface. A standard API/SPI for the Java EE naming interface.
- JORAM
The Java Open Reliable Asynchronous Messaging is an open source implementation of the JMS API built on top of the ScalAgent distributed agent technology and hosted by OW2.
- JORM
Java Object Repository Mapping is an OW2 project that provides an adaptable persistence service.
- JOTM
Java Open reliable Transaction Manager is an open source implementation of the JTA APIs hosted by OW2.
- JPA
Java Persistence API. A Simpler Programming Model for Entity Persistence.
- JSF
JavaServer Faces is a technology that simplifies building user interfaces for JavaServer applications.
- JSP
JavaServer Pages is a technology that provides a simplified, fast way to create dynamic web content.
- JSTL
JavaServer Pages Standard Tag Library. An extension to the JSP specification that adds a tag library of JSP tags for common tasks, such as, XML data processing, conditional execution, loops and internationalization.
- JTA
Java Transaction API. Standard Java interfaces between the transaction manager and the parties involved in a distributed transaction system: the resource manager, the application server, and the transactional applications.
- JRE
Java Runtime Environment.
- JRMP
Java Remote Method Protocol is a Java RMI standard protocol.
- JVM
The Java Virtual Machine.
- JWSDL
Java APIs for WSDL. Provides a standard set of Java APIs for representing, manipulating, reading and writing WSDL (Web Services Description Language) documents, including an extension mechanism for WSDL extensibility.
- Log4j
A Java-based logging utility from the Apache Software Foundation. It is used primarily as a debugging tool.
- Monolog
- MX4J
An Open Source implementation of the Java Management Extensions (JMX) and of the JMX Remote API (JSR 160) specifications.
- P6Spy
An open source Java tool that intercepts and logs all database statements that use JDBC.
- RMI
Remote Method Invocation. This is the java standard specification for RPC technology.
- RPC
Remote Procedure Call is a technology that allows a subroutine or procedure to execute in another address space.
- SAAJ
SOAP with Attachments API for Java. Provides a standard way to send XML documents over the Internet from the Java platform.
- Speedo
An open source implementation of the JDO 1.0.1 specification hosted by OW2.
- Struts
Apache Struts is an open-source framework for developing Java EE web applications. It uses and extends the Java Servlet API to encourage developers to adopt the model-view-controller architectural pattern.
- Tomcat
Apache Tomcat is the servlet container that is used in the official Reference Implementation for the Java Servlet and JavaServer Pages.
- Velocity
The Apache Velocity Engine is a free open-source templating engine.